Cloud security is the practice of protecting cloud computing environments and the data they store, process, and transmit. It combines technologies, policies, and controls that safeguard cloud-based infrastructure, applications, and services from threats, misconfigurations, and unauthorized access. As organizations increasingly migrate workloads to platforms like AWS, Azure, and Google Cloud, protecting these digital assets has become essential for maintaining uptime, data privacy, and regulatory compliance.
At the core of cloud security is a layered, defense-in-depth structure. It begins with perimeter protection using tools such as web application firewalls and intrusion prevention systems. This is followed by strict access governance through identity and access management (IAM), which enforces user authentication and permission boundaries. Data encryption ensures confidentiality both in transit and at rest, while continuous monitoring tools detect unusual behavior and trigger automated responses. Together, these layers form a cohesive security mechanism that adapts to the flexible and distributed nature of cloud environments.
This layered approach is especially critical given that Gartner predicts 99% of cloud security failures by the end of 2025 will be caused by customer errors, primarily misconfigurations and weak access control. The forecast underscores the need for organizations to adopt cloud-native security frameworks that align with the scale, complexity, and shared responsibility model of modern cloud computing.
Table of Contents
Scope of Cloud Security Services in Modern IT Environments
The scope of cloud security Services includes protecting infrastructure, platforms, and applications across a range of deployment models such as public, private, hybrid, and multi-cloud environments. As enterprises shift towards distributed architectures, the need for consistent security controls becomes more urgent.
Darktrace reports that over 70% of enterprises operate in hybrid or multi-cloud configurations, making it essential to secure resources across fragmented systems with unified policies and continuous monitoring. Cloud security services must therefore extend beyond basic perimeter defense to address configuration management, access control, data protection, and compliance enforcement across all layers.
Key areas covered under the scope of cloud security include:
- Infrastructure-as-a-Service (IaaS): Securing virtual machines, containers, and storage resources from external threats and unauthorized access.
- Platform-as-a-Service (PaaS): Protecting development tools, APIs, and platform-managed services used for application deployment.
- Software-as-a-Service (SaaS): Enforcing identity, session control, and data policies within third-party software platforms.
- Hybrid Cloud: Applying consistent security governance across on-premise and cloud systems to reduce integration gaps.
- Multi-cloud Environments: Coordinating security tools and policies across multiple cloud service providers to prevent policy inconsistencies and shadow assets.
What Are the Different Architectures Used in Cloud Security?
Cloud security architecture includes layered security models, Zero Trust frameworks, SASE solutions, cloud-native designs, and micro-segmentation strategies. These architectures define how organizations structure their cloud defenses to manage risks, enforce access controls, and secure dynamic workloads across different environments.
Common architectures used in cloud security include:
- Layered Security Architecture: Applies controls at the network, application, identity, and data layers to prevent single-point vulnerabilities.
- Zero Trust Architecture: Requires continuous verification for every user and device before access is granted, regardless of location.
- Secure Access Service Edge (SASE): Delivers networking and security services, like SD-WAN, CASB, and firewalls, through the cloud to protect distributed users.
- Cloud-native Security Architecture: Built for containerized and serverless environments, integrating security into development and runtime workflows.
- Micro-segmentation: Splits cloud environments into smaller zones to contain threats and restrict lateral movement.
These architectures serve as the foundation for scalable and resilient cloud security operations in both enterprise and hybrid environments.
Cloud Security Architectures Comparison
| Attribute | Zero Trust | SASE | Cloud-native | Layered Model | Micro-segmentation |
|---|---|---|---|---|---|
| Identity Focus | Strict user & device verification | Integrated IAM with edge access control | DevSecOps, container-level roles | Identity layer supported via IAM | Role and zone-based access control |
| Network Scope | Location-agnostic (user/session-based) | Global edge network + SD-WAN coverage | Service mesh, API boundaries | Traditional perimeter + internal zones | Micro-zones with isolated flows |
| Deployment Fit | Ideal for distributed access & hybrid users | Remote branches, SaaS-heavy orgs | Cloud-native apps, serverless workloads | Layered security for large enterprises | High-compliance or east-west sensitive apps |
Cloud Security Layers (Network, Application, Identity)
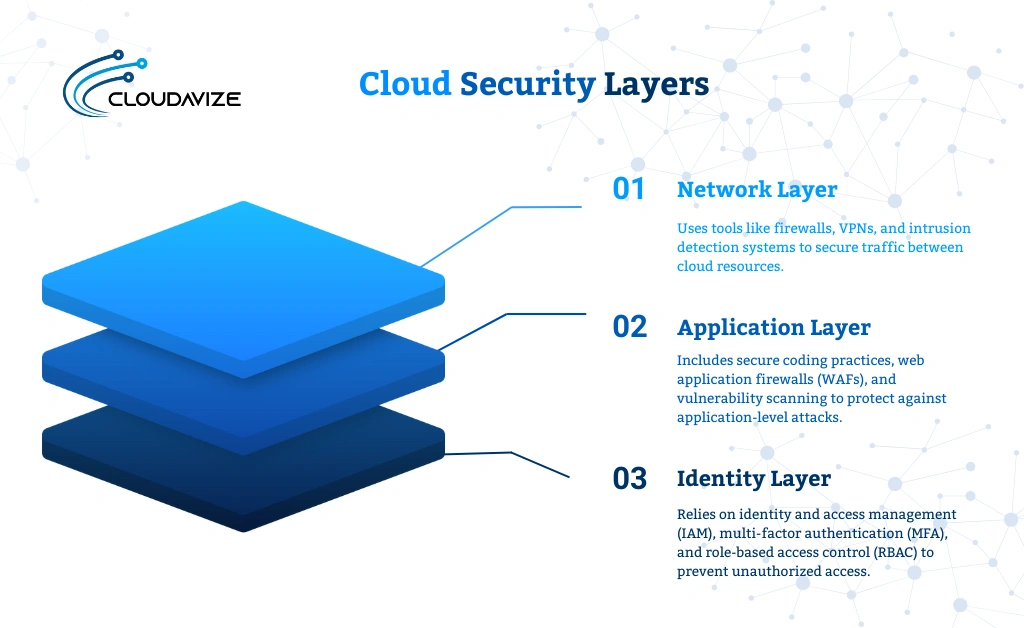
Cloud security follows a layered defense strategy, where each layer, including network, application, and identity, performs a unique security function to reduce the risk of a breach. This multi-tiered approach ensures that if one layer is compromised, others can still protect the environment. These layers work together to enforce segmentation, limit unauthorized access, and monitor threats in real time.
Key components of the layered model include:
- Network Layer: Uses tools like firewalls, VPNs, and intrusion detection systems to secure traffic between cloud resources.
- Application Layer: Includes secure coding practices, web application firewalls (WAFs), and vulnerability scanning to protect against application-level attacks.
- Identity Layer: Relies on identity and access management (IAM), multi-factor authentication (MFA), and role-based access control (RBAC) to prevent unauthorized access.
Zero Trust Architecture
Zero Trust is a cloud security framework that enforces the principle of “never trust, always verify.” It assumes that no user, device, or service should be trusted by default, even if operating within the network perimeter. This model is especially effective in distributed and remote access scenarios, where the traditional perimeter no longer exists.
Core principles of Zero Trust architecture include:
- Verification: Every user, device, and session must undergo strict identity verification before gaining access.
- Least Privilege: Access is limited to only what is necessary for each user or role, reducing the potential impact of misuse..
- Assume Breach: Systems are designed with the expectation that breaches can occur and must be contained.
Secure Access Service Edge (SASE)
SASE integrates network and security functions into a unified, cloud-delivered model to protect users, applications, and data, especially in remote and branch office scenarios. By combining multiple services, SASE allows for simplified policy enforcement and better performance across distributed environments.
Its key components include:
- SD-WAN: Optimizes network performance and routing for remote offices and users.
- CASB (Cloud Access Security Broker): Provides visibility into shadow IT, enforces policy on cloud application use, and protects against data leakage.
- FWaaS (Firewall-as-a-Service): Offers scalable firewall protection delivered entirely from the cloud, without the need for on-premise hardware.
Cloud-native Security Architectures
Cloud-native security is purpose-built for environments using containers, microservices, and serverless functions. It integrates security directly into CI/CD pipelines and runtime environments, enabling protection to scale with infrastructure and application changes.
Common features in cloud-native security include:
- Kubernetes Security: Includes pod security policies, container runtime protection, and role bindings within clusters.
- Serverless Security: Focuses on securing cloud functions, event triggers, and managing execution permissions to prevent privilege escalation.
- Microservices: Uses API gateways, service mesh, and encrypted service-to-service communication to isolate components and enforce policies.
Micro-segmentation in Cloud Environments
Micro-segmentation divides cloud environments into isolated zones to prevent threats from spreading laterally. It provides fine-grained control over communication between workloads and is particularly effective in limiting the spread of threats across the network.
Essential features of micro-segmentation include:
- Network Segments: Separate workloads by function, sensitivity, or compliance level, with traffic restricted between segments.
- Threat Containment: Limits the scope of any potential breach to a small segment.
- Policy Enforcement: Security policies are defined and enforced per segment, enabling audit readiness and improved breach response.
What Are the Different Types of Cloud Security Models?
Main types of cloud security models are public, private, hybrid, multi-cloud, and sovereign cloud. These models determine how security responsibilities are shared between the provider and the customer, and how protection strategies are applied across different environments. As organizations adopt varied cloud setups, choosing the right model becomes essential for aligning controls with infrastructure type, data sensitivity, and regulatory obligations.
- Public Cloud Security: Secures shared platforms like AWS and Azure using provider-managed infrastructure and customer-managed access controls.
- Private Cloud Security: Applies to isolated environments with full control over data, access, and compliance, often hosted on-premise.
- Hybrid Cloud Security: Connects on-premise and cloud systems with unified policies and secure data flow between environments.
- Multi-cloud Security: Manages security across multiple cloud providers with centralized visibility and policy consistency.
- Sovereign and Community Cloud Models: Focus on local data residency, legal compliance, and governance for specific jurisdictions or sectors.
Cloud Adoption by Architecture – 2025 Forecast
Public Cloud Security (AWS, GCP, Azure)
Security in public cloud environments revolves around protecting workloads hosted on infrastructure owned by third-party providers. Platforms like AWS, Microsoft Azure, and Google Cloud offer foundational security for hardware, networking, and hypervisors. However, customers are responsible for securing their applications, identity configurations, and data layers within this shared ecosystem.
To manage this model effectively, businesses must enforce strong access control policies, monitor API traffic, and regularly assess configurations using tools like AWS Config, Azure Security Center, and GCP Security Command Center. Common risks in public cloud setups include overly permissive IAM roles, misconfigured storage buckets, and exposed endpoints. Since these platforms operate on a shared responsibility model, failure to configure them properly places the entire workload at risk.
Private Cloud Security (VMware, OpenStack)
When organizations deploy workloads in private cloud environments, they maintain full control over the security stack. Whether hosted on-premise or through private cloud platforms like VMware or OpenStack, this model provides greater control over resource allocation, network design, and compliance enforcement.
Private clouds allow for custom-built firewalls, dedicated identity management systems, and internal monitoring tools tailored to the business’s needs. Because no infrastructure is shared with external tenants, organizations can align security protocols precisely with frameworks like HIPAA or ISO/IEC 27001. However, the private cloud also requires greater internal expertise and operational overhead to maintain full lifecycle security.
Hybrid Cloud Models
Hybrid cloud environments require security models that can operate seamlessly across both local and cloud infrastructures. This integration introduces complexities around identity management, policy enforcement, and data flow visibility. To manage risks effectively, hybrid models must maintain continuous communication between cloud-based controls and on-premise tools.
Key areas of focus include unified access control, end-to-end encryption during data transfers, and centralized monitoring across platforms. Organizations often use identity federation and network segmentation to maintain security consistency between environments. While hybrid models offer flexibility, they demand careful coordination to avoid security silos or compliance blind spots.
Multi-cloud Environments
Managing security across multiple cloud providers introduces added complexity, requiring organizations to unify their approach. Multi-cloud environments often use services from AWS, Azure, GCP, or others simultaneously, increasing the risk of inconsistent configurations, policy drift, and fragmented monitoring.
Effective multi-cloud security depends on centralized policy orchestration, cross-platform visibility, and standardization of access controls. Security teams often deploy multi-cloud SIEM platforms and cloud security posture management (CSPM) tools to reduce operational gaps. Though multi-cloud strategies offer vendor independence and flexibility, they require a disciplined and coordinated security framework.
Community and Sovereign Cloud Models
Some industries and jurisdictions require cloud environments designed for specialized legal, regulatory, or sectoral needs. Community clouds support shared infrastructure among entities with similar compliance goals, while sovereign clouds ensure all data is stored and processed within specific legal boundaries, often under national oversight.
These models are frequently used by government agencies, defense contractors, or public sector organizations handling sensitive data. Security practices focus on data residency assurance, regulated access, and strict compliance with mandates like GDPR, FedRAMP, or national cybersecurity laws. Although these models offer controlled governance, they often involve higher operational constraints and limited scalability compared to public cloud options.
Cloud Security Models
| Model Type | Deployment Scope | Control Ownership | Use Case Example |
| Public Cloud | Shared cloud (AWS, GCP) | Provider (infra), You (data, apps) | Hosting web apps in AWS |
| Private Cloud | On-prem / hosted | Full enterprise control | Financial sector or military |
| Hybrid Cloud | Cloud + on-prem mix | Shared depending on setup | Merging legacy systems with Azure |
| Multi-Cloud | 2+ cloud vendors | Enterprise via tools | SaaS using AWS & Azure simultaneously |
| Sovereign Cloud | Localized control & compliance | Jurisdiction-defined | Government or EU-specific compliance |
What Tools and Solutions Are Used in Cloud Security?
Cloud security relies on a variety of tools and platforms designed to protect assets across infrastructure, applications, and data layers. These solutions support proactive risk management, ensure policy compliance, and enable organizations to detect and respond to threats in real time. As cloud environments grow more distributed and complex, using specialized tools becomes essential for maintaining visibility, automation, and control.
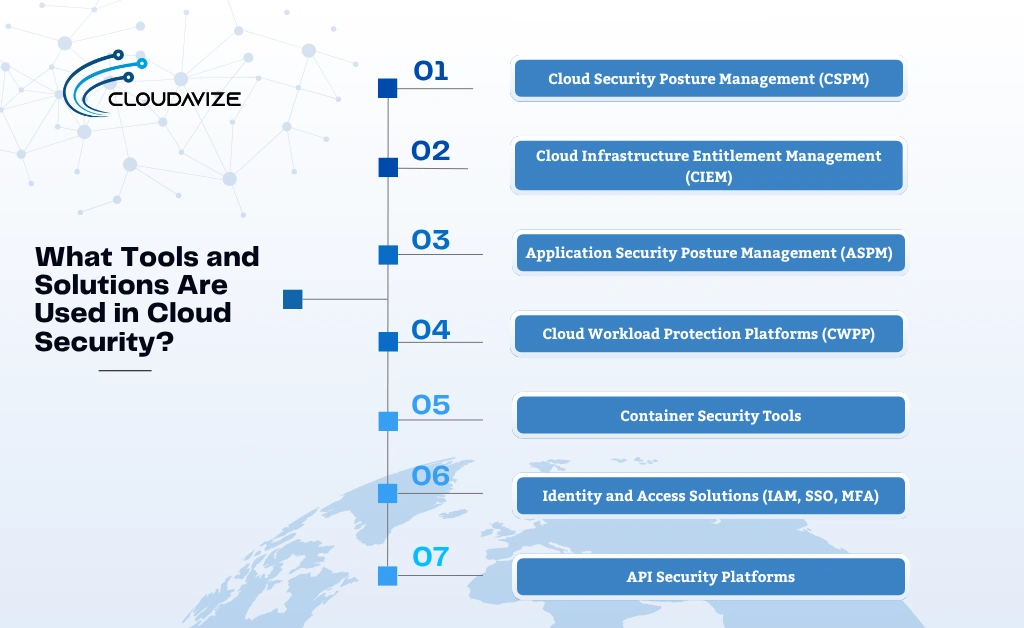
Key cloud security tools and solutions include:
- Cloud Security Posture Management (CSPM) : CSPM tools help identify misconfigurations, enforce security policies, and maintain compliance across cloud accounts. Platforms like Prisma Cloud, Wiz, and Microsoft Defender for Cloud offer automated assessments to reduce risk and ensure alignment with security benchmarks.
- Cloud Infrastructure Entitlement Management (CIEM) : CIEM solutions manage and audit permissions across cloud environments, helping organizations apply least-privilege access principles. Tools such as Ermetic, Sonrai Security, and Microsoft Extra Permissions Management reduce identity sprawl and mitigate privilege-related risks.
- Application Security Posture Management (ASPM) : ASPM focuses on securing applications throughout their lifecycle by detecting misconfigurations, vulnerabilities, and insecure dependencies. Solutions like Apiiro, Snyk, and Palo Alto ASPM integrate with CI/CD pipelines to ensure development-stage security.
- Cloud Workload Protection Platforms (CWPP) : CWPP secures workloads including virtual machines, containers, and serverless functions through runtime monitoring and anomaly detection. Vendors like CrowdStrike Falcon, SentinelOne, and Trend Micro Workload Security deliver protection against fileless attacks and unauthorized behavior.
- Container Security Tools : These tools protect containerized environments by scanning images, securing registries, and enforcing runtime policies. Popular platforms such as Aqua Security, Sysdig Secure, and Anchore help ensure that only trusted containers are deployed in production.
- Identity and Access Solutions (IAM, SSO, MFA) : IAM tools control user authentication and access to cloud resources using role-based access, multi-factor authentication, and centralized identity management. Providers like AWS IAM, Azure Active Directory, Okta, and Duo offer scalable and secure access governance.
- API Security Platforms : API security platforms protect cloud APIs by inspecting traffic, enforcing access policies, and detecting misuse. Tools like Salt Security, Noname Security, and Imperva provide visibility into API behavior and help prevent data exposure.
What are the Benefits of Cloud Security?
The key benefits of cloud security include protecting sensitive data, detecting threats in real time, enabling compliance, and supporting scalable operations. By embedding security into cloud environments, organizations reduce risk, lower costs, and improve control over distributed infrastructure.
Key benefits of cloud security are discussed below:
Enhanced Data Protection
Cloud security strengthens data protection through encryption at rest and in transit, role-based access control, and data loss prevention measures. These safeguards prevent unauthorized access, tampering, and accidental leaks. Common tools include key management services, storage encryption, and cloud-native DLP systems.
Real-Time Threat Detection
Integrated monitoring and analytics enable real-time detection of malicious behavior, anomalies, or access attempts. Threat detection tools generate alerts, correlate events, and trigger automated responses to reduce dwell time. Platforms like AWS GuardDuty or Azure Sentinel are often used for this purpose.
Automated Security Updates
Cloud platforms handle routine patching and updates to infrastructure components without customer intervention. This reduces exposure to known vulnerabilities and eliminates delays common in manual patch cycles. Automation ensures consistent security coverage at scale.
Scalability and Flexibility
Security configurations in the cloud scale automatically with infrastructure. Whether deploying additional workloads or expanding across regions, policies and controls extend seamlessly. This flexibility supports growth without requiring a proportional increase in overhead.
Cost Efficiency and Resource Optimization
Cloud security reduces capital expenditure on hardware-based tools and shifts operational costs to a pay-as-you-go model. Automated processes also reduce staffing burdens by streamlining tasks such as access audits, monitoring, and compliance reporting.
Centralized Visibility and Control
Unified dashboards and logging systems provide end-to-end visibility across cloud assets. Centralized control simplifies auditing, incident response, and compliance tracking across hybrid or multi-cloud deployments, allowing teams to act on accurate and real-time information.
Improved Compliance Alignment
Built-in tools and pre-configured controls support alignment with frameworks like GDPR, HIPAA, PCI DSS, and SOC 2. Security policies can be mapped to specific regulations, with reporting features that assist with audit readiness and ongoing compliance management.
What Are the Common Challenges in Cloud Security?
Most common challenges in cloud security include misconfiguration, identity sprawl, insider threats, and compliance gaps. As cloud environments become more dynamic and distributed, these issues introduce significant risk if not addressed through proper visibility, controls, and automation. Organizations must recognize these challenges early to maintain a secure and resilient cloud posture.
Key challenges in cloud security include:
Misconfiguration and Poor Visibility
Misconfigurations are one of the most frequent causes of cloud security failures, often stemming from poorly secured storage, default settings, or open ports. These issues remain undetected when visibility into cloud assets is limited. Without centralized monitoring or configuration baselines, organizations face prolonged exposure to risk. Tools like CSPM help identify such gaps before they lead to breaches.
Shadow IT and Unauthorized Access
Shadow IT arises when employees use unapproved cloud services outside official IT oversight, making it difficult to track or secure sensitive data. These unmonitored activities bypass established access controls and increase the attack surface. Without discovery tools and usage policies in place, unauthorized access becomes harder to detect and control across cloud environments.
Insider Threats and Human Error
Insider threats often emerge from routine human mistakes or deliberate misuse of privileges. From sharing credentials to mishandling sensitive configurations, user actions can inadvertently expose cloud environments to risk. Without proper identity controls, behavior analytics, or audit logging, these internal actions may go unnoticed until a breach occurs.
Identity Sprawl and Credential Misuse
As cloud usage grows, so does the proliferation of unmanaged identities, duplicate roles, and unused credentials. This identity sprawl creates multiple entry points for attackers and complicates access governance. If permissions are not regularly reviewed or revoked, credentials may be exploited, leading to privilege escalation or data compromise.
Compliance Gaps and Regional Legal Risks
Operating across multiple jurisdictions introduces complex compliance obligations that are often difficult to manage. Misaligned policies, unclear data residency handling, or a lack of region-specific controls can result in violations. Organizations that do not map security configurations to applicable legal standards risk penalties, audit failures, or reputational damage.
What Are the Best Practices for Cloud Security?
Some of the most effective cloud security practices focus on identity control, encryption, secure development, monitoring, and recovery planning. These strategies reduce risks associated with misconfiguration, unauthorized access, and evolving threats. By adopting these practices early, organizations can build resilient cloud environments that support compliance and operational reliability.
Recommended best practices include:
Implementing Identity and Access Management (IAM)
Controlling who has access to cloud resources is the first step in reducing attack surfaces. IAM systems apply role-based access control and enforce least-privilege policies, ensuring users only access what they need. When centrally managed, IAM helps standardize permissions, streamline audits, and prevent privilege misuse across complex multi-cloud environments.
Multi-Factor Authentication (MFA) Strategies
Reinforcing authentication is essential in cloud environments with internet-facing access. MFA enhances account security by requiring a second factor, such as a mobile code or biometric input, in addition to a password. This simple yet effective measure significantly lowers the risk of unauthorized access from compromised credentials.
Data Encryption at Rest and in Transit
Safeguarding sensitive information relies heavily on encryption. Encryption at rest secures stored data using strong ciphers like AES-256, while transport-layer encryption (e.g., TLS 1.2+) protects data during transfer. When properly configured, encryption maintains confidentiality, even in the event of system breaches or unauthorized interception.
Secure DevOps and Shift-Left Security
Securing applications from the start reduces vulnerabilities downstream. A shift-left approach integrates security tools into development workflows, allowing issues to be caught during code writing or build stages. Static analysis, dependency scanning, and container validation all contribute to more secure and compliant deployments.
Continuous Monitoring and Threat Detection
Maintaining real-time visibility across cloud workloads is critical for detecting threats early. Monitoring systems collect logs and behavioral data, feeding threat detection engines that flag anomalies. This constant feedback loop helps security teams respond quickly before minor issues escalate into breaches.
Patch Management and Vulnerability Scanning
Proactively addressing known software flaws limits exploit opportunities. Regular patching and automated updates reduce exposure windows, while scheduled vulnerability scans identify misconfigurations and outdated components. Together, these practices maintain a strong security baseline across evolving cloud environments.
Backup and Disaster Recovery Planning
Protecting availability requires a clear recovery strategy. Frequent backups, distributed storage, and tested recovery procedures ensure that critical data and systems can be restored after an incident. A strong disaster recovery plan minimizes business disruption and supports compliance with uptime and continuity standards.
Cloud Security Best Practices
Apply role-based access control and enforce least privilege across all cloud environments.
Recommended Tools: AWS IAM, Azure AD, Okta, Google Cloud IAMImplement MFA to reduce the risk of account compromise from stolen credentials.
Recommended Tools: Duo Security, Microsoft Authenticator, Google AuthenticatorUse AES-256 encryption for stored data and TLS 1.2+ for data in transit to secure sensitive workloads.
Recommended Tools: AWS KMS, Azure Key Vault, Google Cloud KMSEnable anomaly detection, log collection, and automated alerts to identify potential breaches early.
Recommended Tools: AWS GuardDuty, Azure Sentinel, CrowdStrike FalconIntegrate security testing early in the CI/CD pipeline to catch misconfigurations before deployment.
Recommended Tools: Snyk, Checkmarx, GitHub Advanced SecurityMaintain updated software versions and scan infrastructure routinely for known vulnerabilities.
Recommended Tools: Tenable Nessus, Qualys, Rapid7 InsightVMAutomate backup routines and regularly test disaster recovery procedures for business continuity.
Recommended Tools: AWS Backup, Veeam, Azure Site RecoveryWhat Are the Key Compliance Standards for Cloud Security?
Primary cloud security compliance standards include GDPR, HIPAA, PCI DSS, and others that define how organizations must secure data in cloud environments. These frameworks provide legal and operational benchmarks that cloud providers and users must follow to avoid penalties, protect sensitive data, and maintain trust.
Key compliance standards for cloud security are as follows:
- GDPR, HIPAA, CCPA in Cloud Context – These privacy laws regulate personal and health data in the EU (GDPR), U.S. healthcare sector (HIPAA), and California (CCPA). In cloud deployments, organizations must ensure lawful processing, data access restrictions, and breach notification capabilities using encryption and access controls.
- ISO/IEC 27001, NIST 800-53 Standards – ISO/IEC 27001 sets a global benchmark for managing information security with defined control objectives. NIST 800-53, often used in the U.S., provides a control catalog for federal systems and commercial cloud adoption, focusing on access, audit, and incident response.
- FedRAMP, SOC 2, PCI DSS Alignment – These standards support cloud use in regulated environments. FedRAMP authorizes cloud providers for U.S. government use, SOC 2 assesses trust criteria for SaaS and cloud platforms, and PCI DSS applies to payment systems hosted in the cloud.
- Shared Compliance Responsibility with Cloud Providers – In cloud models, providers handle infrastructure-level controls while customers manage configurations, identity, and application security. This shared responsibility requires clarity on control ownership for audit readiness and security assurance.
- Compliance Automation Tools – Platforms like Wiz, Drata, and Prisma Cloud automate compliance posture monitoring, audit preparation, and policy enforcement across multi-cloud deployments. These tools help maintain real-time compliance and reduce manual overhead.
Cloud Security Services and Providers
Cloud security services include both platform-native tools and third-party providers that offer specialized capabilities such as threat detection, compliance monitoring, and access governance. These help organizations scale their defenses across distributed workloads without overburdening internal teams. From managed detection to security as a service, the modern cloud security stack is built on an ecosystem of interoperable offerings tailored to complex, multi-cloud environments.
Managed Detection and Response (MDR)
MDR services provide 24/7 monitoring, threat hunting, and incident response for cloud environments. Unlike traditional security tools, MDR combines human expertise with analytics platforms to detect and contain advanced threats. Providers like Arctic Wolf and Rapid7 MDR offer cloud-specific coverage, helping teams identify and respond to suspicious activity without building internal SOCs.
Cloud-native Security Services (AWS GuardDuty, Azure Defender)
Public cloud providers offer built-in security services that integrate natively with their platforms. AWS GuardDuty, Azure Defender, and Google Security Command Center provide threat detection, vulnerability assessments, and posture management. These tools are optimized for platform-specific visibility, reducing friction in monitoring and enforcement across services hosted within their ecosystems.
Third-party Threat Intelligence Providers
External threat intelligence feeds enrich cloud security with real-time data on malware signatures, zero-day exploits, and attacker infrastructure. Providers like Recorded Future, Mandiant, and IBM X-Force integrate with SIEMs and XDR tools to improve detection and response capabilities. They help contextualize alerts and prioritize threats based on external risk signals.
Cloud Security Managed Service Providers (MSPs)
Cloud-focused MSPs offer end-to-end security management for organizations lacking in-house expertise. These providers handle configuration auditing, policy enforcement, IAM tuning, and compliance readiness. Companies like Cloudavize, Rackspace, Optiv, and Accenture provide managed cloud security operations tailored to enterprise and SMB needs.
Security as a Service (SECaaS) Models
SECaaS delivers cloud-based security tools such as firewall protection, intrusion detection, DLP, and email security on a subscription basis. This model allows organizations to scale security functions without capital investment in hardware. Common SECaaS offerings include Zscaler for access control, Proofpoint for email security, and Cloudflare for WAF and DDoS protection.
Threats and Vulnerabilities in Cloud Security
Cloud environments face unique security risks that evolve with infrastructure scale, user distribution, and integration complexity. Threat actors exploit cloud-specific weaknesses such as misconfigurations, exposed APIs, and uncontrolled resource provisioning. To maintain a resilient posture, organizations must understand the types of threats that target cloud platforms and implement layered defenses to detect, contain, and respond effectively.
Cloud Malware and Ransomware
Cloud malware specifically targets dynamic workloads, cloud storage, and containerized applications by exploiting misconfigurations or exposed access tokens. Once inside, attackers can deploy ransomware to encrypt data and disrupt business operations. These threats often originate from compromised credentials or third-party access paths, such as CI/CD pipelines, making early detection and identity control essential for prevention.
Denial-of-Service Attacks (DoS/DDoS)
DDoS attacks disrupt availability by overwhelming cloud-hosted services with excessive traffic or malformed requests. They commonly target APIs, DNS services, or public-facing applications, rendering them inaccessible. While providers like AWS and Azure offer built-in DDoS mitigation, additional controls, such as traffic filtering, geo-blocking, and rate limiting, are necessary to ensure service continuity under sustained attack.
Configuration Drift and Shadow IT
Configuration drift occurs when cloud resources gradually deviate from approved security baselines due to manual changes or automated deployments. These unintended variations often go unnoticed, leaving environments exposed. At the same time, shadow IT, tools and services deployed without IT authorization, bypasses governance controls. Together, these risks undermine policy consistency, reduce visibility, and create exploitable gaps in the cloud infrastructure.
Frequently Asked Questions
Why Does Cloud Security Matter?
Cloud security matters because it protects sensitive data, systems, and services in scalable but exposed environments. With most cloud infrastructure publicly accessible by design, strong security ensures business continuity, safeguards user trust, and prevents unauthorized access. It also supports compliance with data protection laws and mitigates risks tied to remote work and multi-cloud expansion.
How Does Cloud Security Differ from Traditional Security?
Cloud security differs from traditional security by focusing on identity, automation, and distributed control rather than perimeter defense. Since cloud environments lack fixed infrastructure, protection is applied through APIs, IAM, encryption, and continuous monitoring. This shift demands a more dynamic, policy-driven approach to securing workloads and access points across platforms.
What is the Role of Zero Trust in Cloud Security?
The role of zero trust in cloud security is to eliminate implicit trust and validate every access attempt. Unlike perimeter-based models, it requires user, device, and application verification regardless of location. This model fits naturally with the cloud’s dynamic structure and helps prevent lateral movement after a breach, especially in environments with high user mobility.
Can Small Businesses Afford Cloud Security Tools?
Yes, small businesses can adopt affordable cloud security through built-in provider tools and flexible pricing models. Solutions like AWS Free Tier, Microsoft Defender for Business, or open-source security platforms offer baseline protection without heavy investment. These options allow smaller teams to enforce access control, monitor assets, and maintain compliance effectively.
Are Cloud Environments Automatically Compliant?
No, cloud environments are not automatically compliant. While cloud providers offer compliant infrastructure, customers are responsible for secure configuration, access management, and data protection. Achieving compliance requires using built-in tools correctly, mapping controls to regulations, and continuously auditing system behavior under the shared responsibility model.
Is Cloud Security better than On-Premise Security?
Cloud security can be more effective than on-premise models due to scalable controls, rapid patching, and integrated threat intelligence. However, its success depends on how well customers implement access policies, encryption, and monitoring. Misconfigured resources in the cloud can create vulnerabilities faster than in fixed, hardware-based systems.



