A cybersecurity checklist is a clear and organized guide that outlines the necessary steps to protect your business from digital threats. It helps ensure that key security measures are applied consistently across systems, data, and networks. In 2025, with cyber attacks becoming more frequent and advanced, using a checklist is essential for reducing risks and staying compliant.
This checklist includes important areas such as cybersecurity governance, security technologies, incident response, and network protection. It also addresses data privacy, third-party risks, and the need to monitor emerging threats. Each section is designed to strengthen different parts of your organization’s security posture. You will also find recommended best practices like backing up data regularly, enabling multi-factor authentication, and installing timely updates that will help your business stay secure and resilient.
Table of Contents
What is Cybersecurity?
Cybersecurity is the process of safeguarding digital systems, networks, and data from cyberattacks. It includes utilizing secure technologies like VPNs, firewalls, and encryption tools, robust security controls like multi-factor authentication (MFA) and access control policies, and proven protocols like TLS (Transport Layer Security) or IPsec to detect, prevent, and respond to data breaches, ransomware attacks, and other real-time malicious activities.
With increasing reliance on interconnected systems such as cloud platforms and IoT devices, and remote operations, businesses need to implement top-notch cybersecurity measures that protect their digital assets, customer information, and ensure business continuity with minimal impact. Lack of effective protection can cause significant risks, ranging from financial loss and reputational damage to loss of customers’ trust and low retention rate.
To fully understand how the presence of reliable cybersecurity benefits modern business, you should check out these 6 key importance of cybersecurity in 2025.
- Reduces the risk of cyber attacks by identifying vulnerabilities and minimizing exposure.
- Maintain compliance with federal, regulatory, and industry-specific regulations.
- Implements incident response plan and recovery process to improve emergency response.
- Simplifies audits and reviews with organized, real-time logs and automated documentation.
- Enforces role-based access control and multi-factor authentication (MFA) to prevent unauthorized access.
- Conducts periodic backups and implements proven recovery protocols to support operational continuity.
With full consideration for strong cybersecurity, businesses should create a proper system that addresses all the critical elements. They must adopt a structured cybersecurity checklist that covers all the crucial defense strategies, ensuring complete protection of the IT infrastructure against sophisticated threats and security risks.
Why is a Cybersecurity Checklist Important?
A cybersecurity checklist is important because it provides a structured, reliable, and comprehensive guide to maintaining the security posture of an organization. It ensures that every aspect of security is covered, allowing businesses to detect gaps and weaknesses, implement best practices, and keep systems updated to shield IT systems and critical data against cybersecurity threats.
Using a cybersecurity checklist enables companies to systematize procedures and protocols, fulfill compliance mandates, and effectively address IT emergencies. Below is the list of 7 crucial reasons highlighting the importance of a cybersecurity checklist for modern businesses.
- Reduces cyber attacks by implementing proactive defences across networks and devices.
- Maintains compliance with regulatory frameworks, including NIST (National Institute of Standards and Technology) standards.
- Improves response during an emergency with a pre-defined incident response plan and data recovery process.
- Simplifies audits and reviews by having accurate records and documented controls for compliance checks.
- Evaluate password management, firewall, and MFA periodically.
- Minimizes downtime by integrating real-time detection systems and automated alerts.
- Mitigates risk by imposing role-based access control while limiting access to unauthorised access.
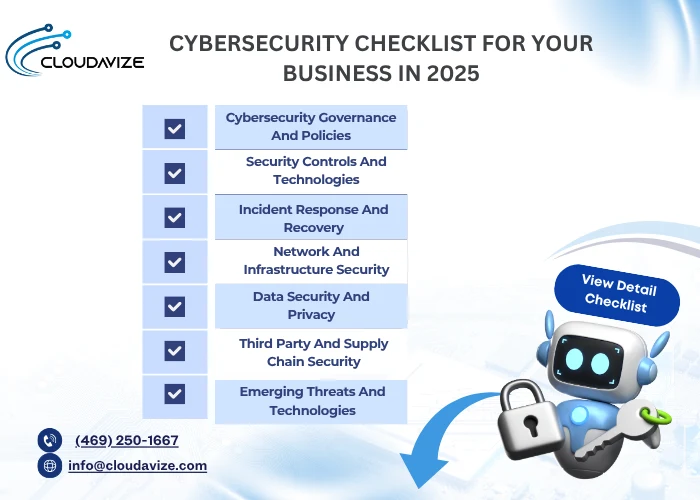
What Are The Key Components of a Cybersecurity Checklist?
The key components of a cybersecurity checklist focus on governance, technologies, response planning, network security, privacy, and vendor management. These critical components form the foundation of the checklist, assisting in the protection of digital systems, compliance management, and the setup of a comprehensive and robust cybersecurity defense strategy.
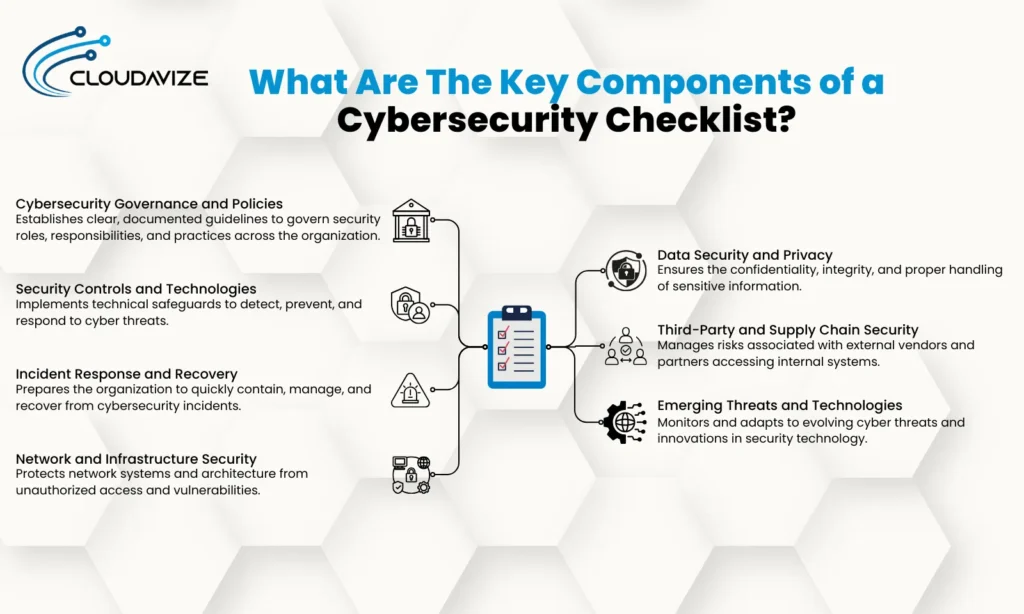
Cybersecurity Governance And Policies
With a focus on establishing clear, documented security policies, this component guides the behavior, access, and responsibilities within an organization. Cybersecurity governance and policies assign roles and responsibilities, and conduct periodic policy reviews across departments. A well-defined governance framework should include the following actions:
- Define a cybersecurity policy approved by leadership.
- Conduct regular cybersecurity risk assessments.
- Conduct periodic security awareness training programs for employees.
- Establish a role-based access control for systems and data.
- Review security policies annually or after major incidents.
Security Controls And Technologies
Serving as the frontline defense against cyber threats, security controls and technologies detect, block, or neutralize unauthorized access attempts before incurring damage. For a solid technical defense layer, businesses should implement these critical control measures:
- Install antivirus/antimalware software and keep it updated.
- Use multi-factor authentication (MFA) for critical systems.
- Implement intrusion detection/prevention systems (IDS/IPS), Security Information and Event Management (SIEM) system, endpoint detection and response (EDR) solution, and firewalls.
- Encrypt all sensitive and confidential data.
- Refrain from the use of unauthorized USB/media devices.
Incident Response And Recovery
An incident response plan paired with an effective and tested recovery process empowers an organization to stay resilient against cybersecurity incidents. It enables businesses to continue operations with rapid containment, minimal disruption, and successful recovery. This component should cover the following steps:
- Develop an incident response plan with clearly defined roles.
- Test the response plan annually or after an incident.
- Document and update incident logs.
- Maintain an updated contact list of the response team.
- Establish a disaster recovery process with tested backups.
Network And Infrastructure Security
Businesses require a reliable security system to secure the network infrastructure against unauthorized access. By monitoring internal and external traffic, organizations can ensure complete protection from attackers. They can apply the following checklist items to maintain a robust and secure architecture.
- Disable unused network services and ports.
- Apply security patches promptly to all systems.
- Use real-time monitoring tools for network activity.
- Isolate the network for different user groups.
- Restrict the use of public Wi-Fi and unsecured connections.
Data Security And Privacy
Organizations are responsible for maintaining the confidentiality and integrity of customer and employee data from unauthorized access and data breaches. They should implement a practical data protection strategy through storage, transmission, and access control by implementing the following actions.
- Identify and categorize sensitive data.
- Encrypt data in transit and at rest.
- Implement data loss prevention (DLP) tools, such as Forcepoint DLP, Digital Guardian DLP, and Microsoft Purview.
- Regularly back up data and test the restoration.
- Retain access and data usage logs.
Third Party And Supply Chain Security
Since businesses require constant connection and interaction with external vendors and service providers, they become a potential attack vector. Therefore, it becomes crucial to evaluate and monitor external regularities regularly to prevent unauthorized access and keep the IT system and infrastructure secure. The checklist should outline the following practices:
- Assess vendor security polices and procedures.
- Limit access provided to third-party suppliers and vendors.
- Monitor vendor activity and access logs.
- Ensure compliance of external parties with internal standards.
- Maintain updated contacts with cybersecurity clauses.
Emerging Threats And Technologies
With technological advancement, new cyber threats also evolve constantly. To tackle these threats and remain updated, vigilant, and adaptive to emerging threats, businesses should monitor technological developments closely and adapt real-time policies for a strong security posture. The checklist advises implementing these steps:
- Monitor ransomware attacks and zero-day threats.
- Educate the team on the latest attack methods by conducting training sessions.
- Subscribe to threat intelligence feeds.
- Update policies to include new risk areas.
- Test the effectiveness of new cybersecurity tools and platforms before deployment.
What Are The Best Practices For Using a Cybersecurity Checklist?
The best practices for using a cybersecurity checklist involve consistent backup of sensitive data, use of strong passwords, implementing MFA, keeping antivirus updated, and creating an emergency management plan. These checklist items should be proactively and consistently applied across areas to align the IT infrastructure with the business risk profile. Consistent application of these cybersecurity practices ensures proper documentation and active enforcement across the organization, strengthening the cybersecurity defense strategy.
- Regularly Back Up Data
Back up all essential business data periodically on secure, off-site storage, or encrypted cloud platforms to avoid permanent data loss. It becomes most useful during the event of hardware failure, ransomware attacks, natural disasters, or other unforeseen incidents.
- Use Strong, Unique Passwords
Establish a strict password policy that requires employees to create complex, unique passwords (a mix of numbers, letters, and symbols) for each account. Avoiding the re-use of the same password across multiple platforms and systems reduces the likelihood of credentials misuse. It helps prevent unauthorized access in case one account is compromised.
- Enable Multi-Factor Authentication (MFA)
Implementing MFA for all accounts with sensitive data and systems adds an extra layer of identity verification. It reduces the risk of credential-based attacks and blocks unauthorized logins, even when a password is misplaced, lost, or stolen.
- Keep Antivirus Software Updated
Always use reputable antivirus software across the systems for your business and keep it up-to-date with the latest threat definitions to detect and remove the latest version of malware accurately. Meanwhile, outdated security software may fail to detect or block new malware variants, leaving your systems exposed.
- Use Firewalls
Set up network and host-based firewalls to inspect and filter in and out traffic. Firewalls are key to blocking unknown connections and controlling access to the network.
- Install Software Updates Promptly
Apply all software updates and security patches as soon as they come out. Delaying updates can leave known vulnerabilities open to attack, allowing attackers to exploit unpatched systems.
- Develop an Emergency Management Plan
Create a clear emergency management plan that outlines how your organization will respond to cyber incidents. This should include designated response roles, recovery steps, and testing the plan regularly to ensure readiness during crises.
How Can Implementing A Cybersecurity Checklist Protect Your Business From Potential Threats?
Implementing a cybersecurity checklist helps protect your business by ensuring proper implementation and maintenance of all essential security protocols. It minimizes the risk of cyber threats, improves your ability to respond to incidents, and supports compliance with industry standards and regulatory requirements.
To support these efforts, many businesses turn to Cloudavize, a trusted cybersecurity partner known for delivering robust, real-time, and practical protection solutions. Cloudavize helps organizations implement and manage their cybersecurity checklist through services like risk assessments, network monitoring, and incident response planning, ensuring continuous defense against evolving threats and vulnerabilities.