A Managed IT Services Checklist is a structured evaluation tool used by businesses to assess potential managed service providers (MSPs) against key operational, technical, and strategic criteria. This checklist outlines essential service areas, such as performance, security, scalability, and support, and ensures that each provider is measured consistently before a final decision is made. Rather than relying on assumptions or surface-level promises, the checklist enables businesses to dig deeper into what each MSP offers, how those services align with business goals, and whether the provider can deliver long-term value.
Choosing the right MSP can determine how well a business handles growth, minimizes risk, and maintains continuity in an increasingly digital and compliance-driven environment. With many providers offering similar claims, a checklist brings clarity and confidence to the decision-making process. It helps organizations identify service gaps, compare vendors objectively, and avoid costly mistakes.
This guide explores every critical component of the checklist, helping you avoid operational risks, maximize return on investment, and ultimately select a reliable managed IT services provider that fits your current needs and upcoming plans.
Table of Contents
What Are Managed IT Services?
Managed IT Services are outsourced IT tasks handled by third-party vendors (MSPs). Managed Service Providers oversee and maintain IT infrastructure and operations under a service level agreement (SLA) that defines monitoring, management, network security, and technical responsibilities. Outsourcing complex IT activities to an MSP helps organizations minimize downtime, reduce costs, improve uptime, enhance operational productivity, and dedicate internal resources to core strategies.
External service providers offer managed IT services in the form of Remote Monitoring and Management (RMM), Managed Cybersecurity Services, Managed Cloud Services, Managed Backup and Disaster Recovery, and IT Help Desk Support. Through these services, MSPs ensure that tech activities align with business objectives for long-term security, compliance, scalability, flexibility, adaptability, and business continuity.
To ensure that MSPs deliver measurable value, organizations rely on a managed IT services checklist that defines major aspects and requirements necessary for correct assessment. This checklist is a practical framework that highlights crucial components offered by MSPs and validates whether these services meet business goals, regulatory demands, and performance expectations.
Why Is a Managed IT Services Checklist Important?
A managed IT services checklist is important for evaluating the services offered by MSPs to ensure they align with business needs. It serves as a strategic guide that helps assess the third-party vendor’s capabilities, responsiveness, and suitability for your organization’s IT requirements. Using a managed IT services checklist helps reduce risk, simplify comparisons, and support confident, data-driven decision-making.
Below are the 10 crucial points that highlight the importance of a managed IT services checklist.
- Vendor Comparison: Enables side-by-side evaluation of service scope, response time, and certifications.
- Performance Assurance: Confirms that MSPs meet operational and service-level benchmarks.
- Strategic Alignment: Matches MSP services with long-term business objectives and growth plans.
- Risk Reduction: Identifies vulnerabilities in security, compliance, and disaster recovery before onboarding.
- Budget Control: Helps assess pricing models and value delivery against defined needs.
- Decision Clarity: Simplifies complex choices with standardized evaluation criteria.
- Regulatory Compliance: Verifies the MSP’s ability to meet industry-specific legal and data protection standards.
- Transparency and Accountability: Establish clear expectations for communication, support, and escalation.
- Operational Consistency: Ensures uninterrupted delivery of essential IT functions.
- Scalability Planning: Evaluates an MSP’s ability to support future expansion and infrastructure changes.
What Are the Key Components of a Managed IT Services Checklist?
The key components of a managed IT services checklist include critical service categories that define the scope, agreement, performance, delivery, compliance, security, expertise, cost-effectiveness, and communication standards of an MSP. These key aspects form the foundation for assessing an MSP on whether they can align IT activities with business, operational, and compliance requirements. By assessing each component of the checklist, businesses can reach a consensus and make risk-aware decisions that ensure long-term growth and performance accountability.
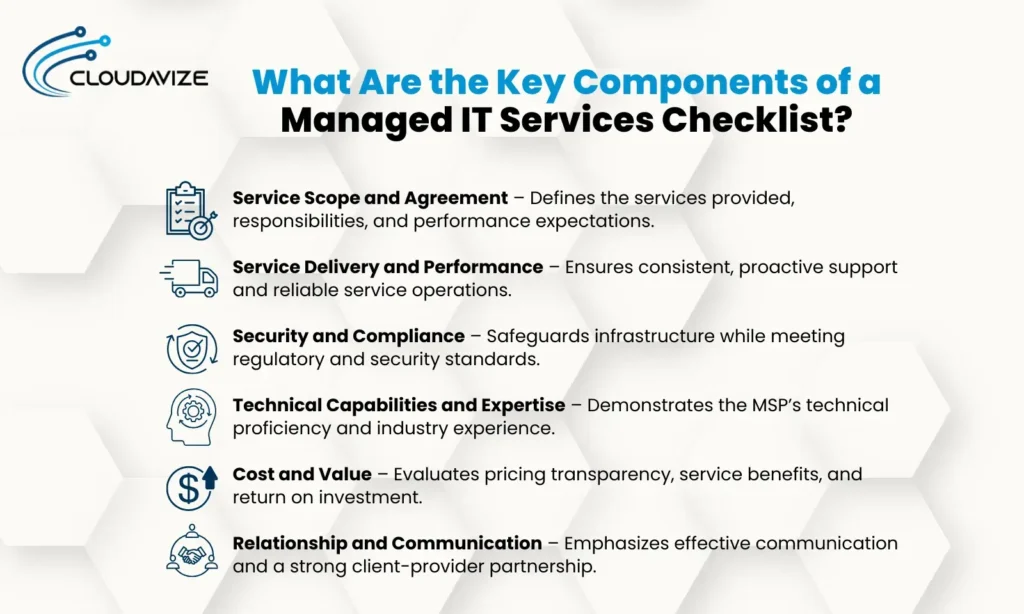
Service Scope and Agreement
With a well-defined service scope and agreement, organizations can set clear expectations regarding what services they receive, their measurement, and the division of responsibilities.
- Review the types of services offered (e.g., cloud, backup, help desk).
- Confirm availability expectations (e.g., 24/7 monitoring, after-hours support).
- Evaluate response and resolution time commitments outlined in the SLA.
- Ensure coverage for routine maintenance, software updates, and patching.
- Assess included and excluded items to avoid scope ambiguities.
Service Delivery and Performance
To ensure business continuity, organizations must choose an MSP that provides reliable service delivery and consistent performance. They should offer reactive and proactive support and must have proven systems to manage, track, and report performance status.
- Verify remote and on-site support availability.
- Assess ticketing system and workflow tracking.
- Check for performance metrics reporting and response time monitoring.
- Review internal escalation procedures for unresolved or critical issues.
- Evaluate automation tools used for service delivery and system updates.
Security and Compliance
Organizations should examine the effectiveness of MSPs in safeguarding IT infrastructure and adhering to applicable regulatory requirements. This helps ensure the quality of the security system in minimizing exposure to legal risks.
- Confirm managed cybersecurity services, including endpoint protection and firewalls.
- Adherent to industry-specific standards, including HIPAA, and PCI-DSS.
- Ask about data encryption, secure remote access, and email security.
- Verify multi-factor authentication (MFA) and access controls.
- Validate incident response planning and vulnerability management.
Technical Capabilities and Expertise
An external provider should showcase its technical strength in managing complex environments and sustaining the impact so it does not have significant consequences for the organization. MSPs should demonstrate their depth in relevant platforms, tools, and certifications.
- Evaluate support for cloud infrastructure, networking, and virtualization.
- Review certifications like Microsoft, Cisco, or VMware.
- Ensure access to dedicated experts or specialized technicians.
- Confirm experience with industry-specific applications or platforms.
- Review case studies and technical references from similar organizations.
Cost and Value
An MSP should provide the services worth your investment. The outcome should be relative to the cost to call it a success. Organizations should consider transparent pricing, clear deliverables, and measurable benefits while considering an MSP’s value.
- Understand the services in each managed IT services plan.
- Confirm the pricing model (e.g., fixed, tiered, or usage-based).
- Assess the hidden or add-on costs such as onboarding fees, travel, or hardware markups.
- Check for flexibility in contract terms and scalability provisions.
- Evaluate reports based on deliverables like downtime reduction and average issue resolution time.
Relationship and Communication
Maintaining a strong and effective communication channel helps build a robust working relationship between MSPs and clients. There should be clear communication regarding escalation protocols and updates which help foster a transparent, responsive, and partnership-oriented mindset among the involved parties.
- Assess the MSP’s communication cadence (e.g., regular check-ins, and reporting).
- Analyze escalation processes for unresolved issues.
- Examine transparency in documentation, ticket handling, and project updates.
- Confirm availability of desiccated account manager.
- Enquire about feedback channels for service review and improvements.
What Challenges Do Businesses Face and How Can MSPs Help?
Businesses face a range of operational, technical, and compliance-related difficulties that result in downtime, unauthorized access, and other security threats, limited scalability options, financial restrictions, and non-compliance. Partnering with an MSP helps organizations address these pain points with precision, enabling them access to IT experts who help increase uptime, secure network, systems, and infrastructure, scale business with the company’s growth, and make strategic budgeting.
- Limited IT Expertise
Many small and medium-sized businesses (SMBs) lack the in-house IT team to manage and maintain their modern IT systems. Hiring an MSP allows them to fill this technological gap and provides them with specialized support, access to certified professionals, and expert guidance on infrastructure planning and execution.
- Downtime and Technical Disruptions
Without a proper IT roadmap, businesses are likely to experience unplanned downtime which hampers productivity and damages customer trust. However, organizations partnering with MSPs have experts working to reduce downtime through 24/7 monitoring, rapid incident response, and proactive maintenance, ensuring operational continuity.
- Cybersecurity Threats
As cyber risks evolve with the changing IT landscape, businesses struggle to shield their sensitive data and systems. This often results in data breaches, unauthorized access, data theft, credentials misuse, and ransomware, all questioning the organization’s credibility and damaging reputation. But, with MSPs providing managed cybersecurity services through threat detection, firewall management, endpoint protection, and incident response planning, companies can focus on core functionalities without worrying about security incidents.
- Scalability Constraints
As businesses expand, they require flexible IT infrastructure that can scale with their growing operational demands. To meet the scalability needs, MSPs provide cloud services and virtualization, allowing companies to scale seamlessly without compromising their changing demands and performance.
- Budget Constraints
Not all businesses have huge IT budgets. Specifically, SMBs and startups often experience various limitations due to IT budgets, resulting in compromised performance and output. MSPs solve these issues by providing predictable cost models and customized pricing to deliver value-driven plans that align with budget goals while helping organizations access essential services without massive upfront investments.
- Compliance and Data Privacy
Regulated industries like retail, healthcare, and finance find it difficult to navigate different safety and regulatory requirements. Failure to comply or operate within set standards leads to legal disputes, monetary penalties, and closure. Working with MSPs ensures the implementation of data protection policies that maintain regulatory alignment and support audit readiness.
- Complex Vendor Management
Businesses with multiple products/services handling humongous workloads across different locations find it challenging to manage multiple IT vendors. This often leads to fragmented services and communication gaps. Therefore, teaming up with an MSP helps organizations consolidate technology support into a single point of accountability, streamlining service delivery and improving operational efficiency.
How Do You Use This Checklist Effectively?
You can use a managed IT services checklist effectively by following a structured evaluation process that aligns the provider’s capabilities with business needs. Follow this step-by-step method to experience a comparative, informed selection for smooth onboarding.
- Evaluate Your IT Needs
Start by reviewing your existing IT infrastructure, gaps, and long-term business goals. Use the checklist to identify areas for improvement in security, scalability, or cost control and map these needs to the services MSPs offer.
- Compare MSPs Against the Checklist
Use the checklist as a benchmark when selecting potential providers. Ask detailed questions and request proof such as case studies, certifications, and documented response times.
- Score and Shortlist Providers
Rate each MSP against the checklist, focusing on both critical and value-added services. This will eliminate unsuitable vendors early and give you a focused shortlist of providers that can meet your technical and operational requirements.
- Make a Decision Based on Fit
Beyond capabilities, evaluate the MSP’s communication, flexibility, and cost transparency. Choose the service provider that best fits your business culture, expectations, and future growth plans.
- Plan for Onboarding
Use the checklist during the onboarding phase to confirm all service terms and deliverables are implemented. Set performance benchmarks, review timelines, and ensure the MSP is accountable from day one.
Why Choose Cloudavize as Your Managed IT Services Provider?
Choosing Cloudavize means partnering with a reliable and experienced managed IT services provider that understands the importance of performance, security, and accountability. With a strong track record in minimizing downtime, resolving technical issues quickly, and aligning IT operations with business goals, Cloudavize offers dependable support backed by proven expertise.
Cloudavize provides a full range of services, including network security, cloud management, disaster recovery, and help desk support, under a transparent pricing model with no hidden fees. Positive client testimonials reflect satisfaction with the company’s responsiveness, communication, and results-driven approach, making Cloudavize a trusted choice for businesses seeking long-term IT stability and value.




