Table of Contents
What is a Network Security Checklist?
A network security checklist is a structured guide used to protect infrastructure and identify vulnerabilities, risks, and security gaps. It provides a consistent framework for applying essential controls, standardizes security practices, and reduces operational risks across the organization.
An effective checklist covers wireless security, internal access controls, perimeter defenses, remote access, device hardening, monitoring, documentation, and DNS/DHCP protection. To remain useful, it should be customized to fit the environment, prioritized around critical vulnerabilities, and updated regularly to adapt to evolving threats.
Integrating the checklist into audits, onboarding, and offboarding processes reinforces accountability and operational consistency. When aligned with broader security policies and incident response strategies, it creates a cohesive defense model that helps organizations maintain continuity, uphold data integrity, and meet regulatory compliance standards.
What is Network Security?
Network security is the practice of protecting networks from unauthorized access, misuse, modification, intrusions, and data loss.
Its primary objective is to safeguard digital assets during transmission or storage by enforcing confidentiality, integrity, and availability principles. Network security integrates hardware defenses, software protections, and human intelligence, such as incident responders and security analysts, to build resilient protection layers.
Through the deployment of firewalls, intrusion detection systems, encryption protocols, and multi-factor authentication, organizations prevent cyber threats like hacking, malware infections, data breaches, and denial-of-service attacks. A strong network security strategy ensures business continuity, maintains customer trust, and supports regulatory compliance across operational environments.
To build an effective network security framework, organizations should follow a structured checklist that addresses critical protection layers, monitoring standards, and response protocols.
Why is a Network Security Checklist Important?
A network security checklist is important to provide a clear and organized approach to securing an organization’s digital infrastructure. It helps maintain operational continuity, safeguard data integrity, and ensure compliance with regulatory standards. By outlining critical protection measures, the checklist enables organizations to proactively identify vulnerabilities, enforce consistent security practices, and respond effectively to evolving cyber threats.
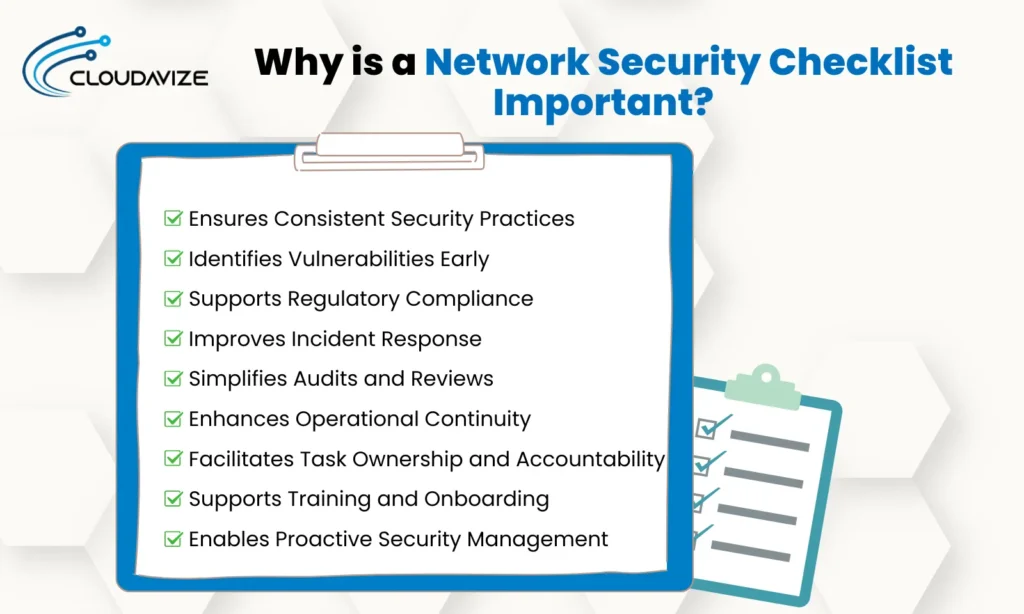
Here’s a list of the importance of network security checklists:
- Ensures Consistent Security Practices: Standardizes procedures across the organization.
- Identifies Vulnerabilities Early: Detects weak points before exploitation.
- Supports Regulatory Compliance: Aligns security efforts with GDPR, HIPAA, ISO, and more.
- Improves Incident Response: Reduces downtime during breaches.
- Simplifies Audits and Reviews: Clear documentation and traceability.
- Enhances Operational Continuity: Minimizes disruptions by securing critical systems.
- Facilitates Task Ownership and Accountability: Defines responsibility clearly.
- Supports Training and Onboarding: Acts as an educational resource.
- Enables Proactive Security Management: Encourages ongoing improvements.
What Are The Key Components of a Network Security Checklist?
The key components of a network security checklist include network perimeter defenses, internal network controls, and wireless access points. These components address remote access protection, device hardening, traffic monitoring, and service layer security for DNS and DHCP systems. Proper functioning and collaboration of these components ensure resilient infrastructures, simplified compliance, and operational continuity in increasingly complex environments.
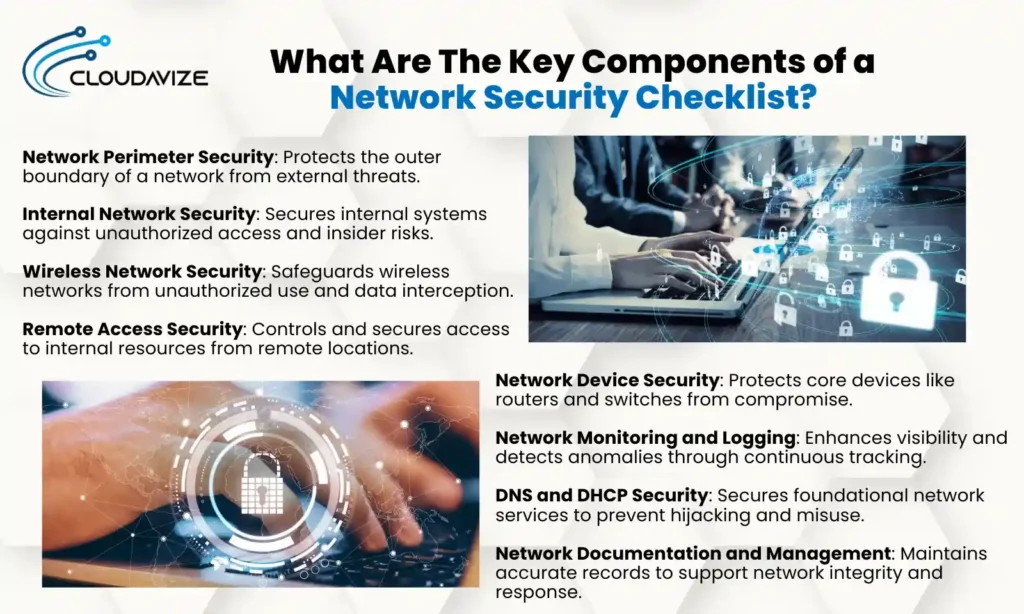
Network Perimeter Security
Protecting the outer boundary of a network through network perimeter security is essential for defending against unauthorized external access. Organizations can strengthen their perimeter by implementing several foundational practices:
- Deploying and arranging firewalls to filter traffic.
- Implement Intrusion Detection and Prevention Systems (IDS/IPS) to detect and prevent intrusions.
- Using Network Address Translation (NAT) to mask internal IPs.
- Disabling unused services and ports on boundary devices.
- Establish a DMZ (Demilitarized Zone) for public-facing applications.
Internal Network Security
Safeguarding internal systems from unauthorized access and insider threats is the primary goal of internal network security. Several critical steps help ensure strong protection within the internal environment:
- Enforce Role-Based Access Control (RBAC) and the Least Privilege Principle.
- Segment internal networks and encrypt sensitive communications.
- Regularly review user access and authentication logs.
- Detect and respond to insider threat indicators.
Wireless Network Security
Given the broadcast nature of wireless signals, wireless network security plays a vital role in minimizing unauthorized access and protecting sensitive communications. Organizations should apply the following measures to secure wireless environments:
- Change the default SSID and administrative passwords on access points.
- Enable WPA3 (or at minimum WPA2) encryption.
- Disable unnecessary SSID broadcasting.
- Segment guest Wi-Fi from production networks.
- Apply MAC address filtering and implement strong authentication protocols like RADIUS.
Remote Access Security
Controlling external entry points effectively falls under remote access security, ensuring that only authenticated users and trusted devices access internal resources remotely. Essential practices for securing remote access include:
- Implement Multi-Factor Authentication (MFA) for all remote sessions.
- Restrict remote access to known IPs and registered devices.
- Use VPNs with strong SSL or IPsec encryption.
- Regularly inspect and monitor remote sessions for suspicious activity.
- Disable unnecessary or legacy remote access services.
Network Device Security
Maintaining the integrity of routers, switches, and firewalls is critical in network device security, protecting devices that form the backbone of network infrastructure. Organizations should adopt the following actions:
- Apply the latest firmware and security patches promptly.
- Change default administrator credentials.
- Disable unused services, interfaces, and ports.
- Enable encrypted management protocols like SSH and HTTPS.
- Backup device configurations securely and audit access regularly.
Network Monitoring and Logging
Enhancing visibility across network activities relies on effective network monitoring and logging, allowing early detection of anomalies and strengthening incident response. Important steps to implement include:
- Monitor network traffic for unauthorized activity.
- Centralize logs using a Security Information and Event Management (SIEM) platform.
- Regularly review and analyze security logs.
- Set automated alerts for critical security events.
- Securely retain logs for compliance and forensic needs.
DNS and DHCP Security
Protecting service layers like DNS and DHCP is the focus of DNS and DHCP security, ensuring trusted communication paths within a network. Organizations can reduce risks associated with service hijacking by following these steps:
- Isolate DNS and DHCP servers from public networks.
- Implement DNSSEC and DNS filtering technologies.
- Monitor DNS/DHCP traffic for unauthorized activity.
- Use IP/MAC binding and restrict DHCP address pools.
- Regularly patch the DNS/DHCP server software.
Network Documentation and Management
Maintaining accurate infrastructure records is central to network documentation and management, supporting visibility, consistency, and fast incident response. Critical documentation practices include:
- Record IP schemes, VLANs, access policies, and user roles.
- Maintain updated network diagrams showing data flows and device links.
- Track firmware, patch histories, and configuration changes.
- Secure documentation repositories with access controls.
- Log all network modifications with timestamps and the responsible personnel.
What Are The Best Practices of Using a Network Security Checklist?
The best practices for using a network security checklist involve customizing the checklist to fit your operational landscape, prioritizing high-risk areas, and regularly reviewing and updating controls. Incorporating task ownership, validation testing, and alignment with broader security policies ensures the checklist remains practical, adaptive, and effective against evolving cyber threats.
- Customize the Checklist to Fit Your Environment:
Tailoring the checklist to your IT environment aligns it with operational goals, infrastructure, and compliance requirements. This approach eliminates unnecessary steps and focuses security efforts on real-world risks.
- Prioritize Critical Security Measures
Focusing on high-risk vulnerabilities first, such as remote access, patch management, and perimeter defenses, reduces breach potential. Prioritization ensures limited resources are used effectively, especially during urgent audits or incident response.
- Regularly Review and Update the Checklist
Updating the checklist frequently keeps it aligned with emerging threats, regulatory changes, and past incident learnings. This practice maintains proactive defenses and prevents security gaps from forming.
- Use the Checklist During Scheduled Audits
Applying the checklist during audits verifies that all critical controls are active and effective. It also highlights areas for improvement and supports regulatory documentation and internal accountability.
- Integrate Zero Trust Architecture (ZTA) Principles
Modern security demands adopting Zero Trust Architecture (ZTA) by verifying explicitly, enforcing least privilege access, assuming breach, and using micro-segmentation to limit lateral movement. Continuous monitoring and validation are essential, and organizations should also consider Secure Access Service Edge (SASE) models to unify networking and security for remote and cloud environments.
- Assign Clear Ownership for Each Task
Delegating responsibility for each task ensures accountability and coordinated execution. Clear ownership prevents critical activities from being overlooked and strengthens proactive security management.
- Incorporate Checklist Use Into Onboarding and Offboarding
Integrating checklist practices during employee onboarding and offboarding reduces the risk of unauthorized access or data loss. It also reinforces the consistent application of security protocols at workforce entry and exit points.
- Validate Controls Through Testing
Regular testing through vulnerability scans, penetration tests, or simulations confirms the effectiveness of security measures. This step builds trust in the checklist and drives continuous improvement.
- Align the Checklist With Broader Security Policies and Plans
Connecting the checklist with overall security policies and response strategies ensures consistent enforcement across all layers. It also supports adaptability as business needs, threats, and regulatory frameworks evolve.
How Can Implementing a Network Security Checklist Ensure Operational Continuity, Data Integrity, and Regulatory Compliance?
Implementing a network security checklist helps organizations maintain operational continuity by detecting threats early and minimizing downtime. It protects data integrity through enforced encryption, backups, and access controls, while also supporting compliance with frameworks like ISO, HIPAA, and GDPR.
For businesses seeking expert support, Cloudavize provides comprehensive network security services designed to ensure frameworks remain reliable, secure, and compliant. Our services help organizations maintain seamless operations through proactive monitoring, policy enforcement, and detailed risk assessments, allowing businesses to stay protected while achieving operational resilience and regulatory readiness.