As businesses handle increasing volumes of sensitive data, from customer details to financial records, the risks of cyber threats grow exponentially. Cybersecurity is crucial to protect this data and ensure that systems remain operational in the face of evolving cybercrime. Cybercrime Magazine projects cybercrime costs to reach $10.5 trillion annually by 2025, highlighting the need for robust security. Without proper protection, businesses face financial losses, legal penalties, and reputational damage.
The cyber threat landscape is growing more sophisticated, with attackers using methods such as ransomware, phishing, and malware to exploit vulnerabilities. Protecting against these threats requires a comprehensive, proactive approach, including advanced security tools, employee training, and continuous system monitoring. Industries, from healthcare and finance to retail and government, should transition from basic defense to a proactive, layered cybersecurity strategy to defend against increasingly complex attacks.
Core components like network security, endpoint protection, and application security work together to mitigate risks. Best practices such as strong passwords, multi-factor authentication, and software updates are essential. A solid cybersecurity strategy reduces the likelihood of an attack and builds trust with customers, ensures regulatory compliance, and supports long-term business stability. For businesses seeking comprehensive protection, partnering with a Managed Service Provider (MSP) can provide the expertise, resources, and proactive monitoring needed to safeguard against ever-evolving cyber threats.
Table of Contents
What is Cybersecurity?
Cybersecurity refers to the practices and technologies used to protect systems, networks, and data from digital attacks. It involves securing not just hardware and software, but also processes, networks, and even people, ensuring that all aspects of a business’s digital presence are protected.
From malware and phishing to more advanced attacks like ransomware, cybersecurity aims to mitigate the risks posed by these threats. By implementing layers of defense such as firewalls, encryption, multi-factor authentication, and continuous monitoring, the healthcare, retail, manufacturing, and finance industries can protect sensitive data from unauthorized access, minimize operational downtime, and reduce the financial impact of potential breaches.
Understanding cybersecurity is just the beginning. To truly protect against evolving cyber threats, businesses must explore deeper practices, recognize the types of threats, and adopt effective defensive strategies to safeguard their digital assets and ensure lasting protection.
Why is Cybersecurity Important?
Cybersecurity is crucial to protect businesses from financial losses, data breaches, and operational disruptions caused by cyberattacks. Without proper security measures, companies risk losing sensitive information, facing significant downtime, and incurring high costs from legal penalties and damage control. As cyber threats continue to evolve, businesses must safeguard their networks, systems, and data to maintain smooth operations and protect their reputation.
Here are some key reasons why cybersecurity is critical:
- Prevents Financial Loss: Cybersecurity measures, like encryption and intrusion detection, help prevent financial losses from attacks such as ransomware, minimizing remediation costs, legal fees, and fines.
- Maintains Business Continuity: By implementing disaster recovery plans and robust network security, cybersecurity ensures that systems stay operational during attacks, reducing downtime and minimizing operational disruptions.
- Safeguards Reputation: Cybersecurity strategies, such as encryption and access control, safeguard valuable intellectual property from unauthorized access and theft.
- Ensures Regulatory Compliance: By securing sensitive data, cybersecurity ensures businesses comply with legal and regulatory requirements, protecting against non-compliance penalties.
- Protects Intellectual Property: Cybersecurity strategies, such as encryption and access control, safeguard valuable intellectual property from unauthorized access and theft.
Types of Cyber Threats
Cyber threats take many forms, including malware, phishing, ransomware, and social engineering. Each of these threats can have severe consequences, causing operational disruptions, significant financial losses, reputational harm, and potential legal liabilities. Recognizing these threat types is crucial for developing a robust defense strategy that reduces risks, safeguards valuable assets, and ensures business continuity in the face of evolving cyber dangers.
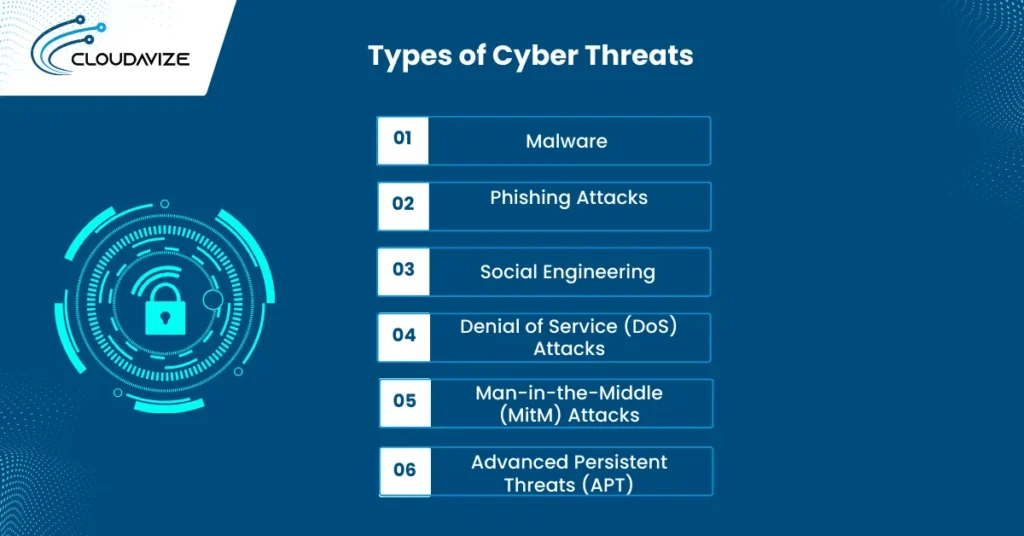
Malware
Malware is malicious software created to harm, exploit, or disrupt systems, often leading to data theft, system failure, and financial losses. It can take various forms, each with unique characteristics and attack methods. Understanding the different types of malware is crucial for preventing their impact and ensuring business security.
Here are some common types of malware:
- Viruses: Attach to files and spread when executed, often corrupting data and slowing down systems.
- Worms: Self-replicating and spread across networks, causing widespread damage and network congestion.
- Trojans: Disguise as legitimate software to steal data or grant unauthorized access.
- Spyware: Secretly monitors user activity and collects sensitive information without consent.
- Ransomware: Locks files and demands payment for access, often causing significant downtime and financial strain.
To defend against malware, businesses must use antivirus software, implement regular system updates, and maintain secure networks.
Phishing Attacks
Phishing is a cyberattack that tricks individuals into revealing sensitive information, such as login credentials or financial details, by impersonating a trustworthy source. It often involves deceptive emails or websites that lure victims into compromising their security.
Some common types of phishing attacks are:
- Email Phishing: Fraudulent emails impersonating legitimate entities to steal data.
- Spear Phishing: Targeted, personalized phishing attacks aimed at specific individuals or organizations.
- Whaling: Targets high-level executives, often involving financial transactions.
- Smishing: Phishing via SMS or text messages to steal personal data.
- Vishing: Phishing over the phone to gather sensitive information directly from the victim.
To protect against phishing, businesses should implement robust email filtering systems, provide regular employee training on recognizing phishing attempts, and adopt multi-factor authentication (MFA) for an added layer of security.
Social Engineering
Attackers often use social engineering to manipulate individuals into disclosing confidential information or granting system access by exploiting human behavior. These attacks often bypass traditional security defenses by relying on trust and emotional manipulation.
Here are common types of social engineering attacks:
- Pretexting: Creating fake scenarios to gain personal information.
- Phishing: Sending fraudulent emails or messages to steal sensitive data.
- Baiting: Offering something enticing to lure victims into downloading malicious software.
- Tailgating: Following authorized personnel into secure areas without proper credentials.
- Impersonation: Posing as trusted figures to gather confidential information.
To protect against social engineering, businesses should implement security awareness training, clear protocols, and multi-layered authentication systems.
Denial of Service (DoS) Attacks
A Denial of Service (DoS) attack disrupts access to services or systems by overwhelming them with excessive traffic or exploiting system vulnerabilities. These attacks can cause significant downtime, halting business operations and damaging customer trust.
Below are key types of DoS attacks:
- SYN Floods: Overwhelm servers by sending excessive connection requests.
- UDP Floods: Use large volumes of UDP packets to consume network bandwidth
- DNS Amplification: Exploits DNS servers to overwhelm the target with traffic.
- Application Layer Attacks: Target vulnerabilities in web applications to crash servers.
To defend against these attacks, businesses should deploy network traffic monitoring, use DDoS protection services, and implement rate-limiting techniques to ensure systems remain functional during traffic surges.
Man-in-the-Middle (MitM) Attacks
When attackers intercept and manipulate communication between two trusted parties, it is known as a Man-in-the-Middle (MitM) attack. This type of cyber threat can be used to steal sensitive data, alter transactions, or impersonate one of the trusted parties. MitM attacks often occur on unsecured networks, such as public Wi-Fi, where attackers can intercept the data transmitted between the user and a website or application.
Common types of MitM attacks are:
- Session Hijacking: Stealing a session token to gain unauthorized access.
- Packet Sniffing: Capturing unencrypted network traffic to steal sensitive data.
- SSL Stripping: Downgrading secure HTTPS connections to unencrypted HTTP.
- DNS Spoofing: Redirecting users to malicious websites to steal credentials or install malware.
To protect against MitM attacks, businesses should use HTTPS, VPNs for secure connections, and enforce multi-factor authentication (MFA) to safeguard data during transmission.
Advanced Persistent Threats (APT)
APTs are targeted, long-term cyberattacks that aim to steal sensitive information or maintain unauthorized access over extended periods. Unlike traditional attacks, APTs are stealthy, often remaining undetected while attackers gather intelligence or exploit systems from high-value assets like government data or corporate secrets.
Here are key characteristics of APTs:
- Long-Term Intrusion: Attackers maintain access over extended periods to gather data.
- Credential Harvesting: Stealing credentials to escalate privileges and access critical systems.
- Data Exfiltration: The primary goal is to steal valuable data, such as intellectual property.
- Evasion of Detection: APTs use tactics like encryption and stealthy malware to avoid detection.
To defend against APTs, businesses should implement network segmentation, continuous monitoring, threat intelligence, and advanced endpoint detection and response (EDR) systems.
What are the Key Components of Cybersecurity?
The core types of cybersecurity include network security, application security, endpoint security, data security, and operational security. Each type addresses specific security needs to protect systems, data, and networks. These components form a comprehensive cybersecurity strategy to defend against various cyber threats.

Network Security
Effective network security is crucial for preventing unauthorized access and ensuring data confidentiality. This involves a combination of strategies and tools that monitor, control, and filter network traffic to detect and block malicious activities, ensuring that only authorized users and devices can access sensitive information.
Key types of network security include:
- Firewalls: Block unauthorized traffic while allowing legitimate communication.
- Intrusion Detection and Prevention Systems (IDS/IPS): Detect and prevent malicious activity by monitoring network traffic for signs of potential threats.
- Virtual Private Networks (VPNs): Encrypt network traffic to secure data during transmission.
- Network Segmentation: Divides the network into smaller segments to limit the spread of attacks.
- Traffic Monitoring: Continuously monitors network traffic for anomalies, helping to detect and block suspicious activities.
Additionally, implementing zero-trust networking principles and employing continuous traffic analysis and anomaly detection are crucial for identifying potential threats in real-time, strengthening overall network security.
Application Security
Application security involves protecting software applications from security threats that can exploit vulnerabilities in their code or design. By integrating security throughout the software development lifecycle (SDLC), businesses can reduce the risk of data breaches and system compromises.
Some critical elements of application security are:
- Secure Coding Practices: Implementing input validation and authentication controls to prevent vulnerabilities like SQL injection and cross-site scripting (XSS).
- Vulnerability Scanning: Regularly scanning applications for security flaws that attackers could exploit.
- Threat Modeling: Using frameworks like the OWASP Top 10 to identify and address the most critical application security risks.
- Testing Types: Using SAST, DAST, and fuzzing to identify and fix vulnerabilities early in the development lifecycle.
- DevSecOps: Shifting security left in the SDLC, ensuring security is integrated early in the development process rather than added later.
Information Security
The protection of data confidentiality, integrity, and availability, known as the CIA triad, is essential for safeguarding sensitive information from unauthorized access, alteration, or loss. Ensuring that data remains secure and accessible only to authorized individuals is critical to preventing breaches and maintaining business continuity.
Core elements of information security are:
- Encryption: Protects data in transit and at rest, ensuring it remains unreadable to unauthorized parties.
- Access Controls: Limits access to sensitive data, ensuring only authorized individuals can view or modify it.
- Data Loss Prevention (DLP): Prevents unauthorized transmission or loss of critical data.
- Data Classification Frameworks: Categorize data into different levels of sensitivity (e.g., PHI, PII, IP) to apply appropriate security measures based on sensitivity.
By implementing strong information governance practices and complying with regulations like GDPR and HIPAA, businesses can protect data while meeting legal and industry requirements.
Operational Security
Operational security (OpSec) focuses on securing the processes and decisions that protect critical information within an organization. It involves identifying and managing risks associated with the handling, storage, and access to sensitive data.
Key areas of OpSec include:
- Access Control: Regulates who can view or modify sensitive data based on user roles.
- Change Control: Ensures that system changes are authorized and do not introduce vulnerabilities.
- Role-Based Access: Granting access based on the specific roles and responsibilities of individuals within the organization.
- Logging/Auditing: Monitoring and recording system activities to detect suspicious behavior or security breaches.
- Staff Segmentation: Limiting access to critical information by segmenting staff responsibilities to minimize risk exposure.
Likewise, the principle of least privilege ensures employees only have access to the information necessary for their duties. Security policies and procedures are essential in maintaining consistent OpSec practices, helping to reduce both insider and external threats.
Disaster Recovery & Business Continuity
Disaster recovery (DR) focuses on the technical restoration of systems and data after an incident, while business continuity (BC) ensures operational processes continue, even during disruptions. Both are critical components of an organization’s ability to withstand cyberattacks, natural disasters, or system failures.
The core components of Disaster Recovery and Business Continuity are:
- Disaster Recovery Plans: Procedures to restore systems, applications, and data after an incident.
- RTO/RPO Metrics: Recovery Time Objective (RTO) defines acceptable downtime, while Recovery Point Objective (RPO) specifies acceptable data loss.
- Backup Strategies: Regular data backups ensure quick recovery in case of an incident.
- Failover and Crisis Communications: Systems that automatically switch to backup resources and ensure communication during an incident.
- Business Continuity Components: Alternative workflows or relocation plans to maintain operations during system outages.
Aligning DR/BC plans with compliance frameworks like ISO 22301 and NIST 800-34 ensures cyber resilience and meets legal and regulatory requirements.
Endpoint Security
Protecting endpoint devices, such as laptops, desktops, and mobile phones, against exploitation is crucial for maintaining overall cybersecurity. These devices often serve as entry points for malware and other cyberattacks, making endpoint security essential.
Key aspects of securing endpoints include:
- Endpoint Protection Platforms (EPP): Provide antivirus, anti-malware, and firewall protection to prevent known threats.
- Endpoint Detection & Response (EDR): Continuously monitors for suspicious activities, enabling quick detection and response.
- Patch Management: Regular software updates to fix vulnerabilities and reduce attack surfaces.
- Mobile Threat Defense (MTD): Protects mobile devices from threats such as phishing, malware, and unauthorized access, especially with the rise of mobile workforces.
- BYOD Management: Secures personal devices used in the workplace by implementing security policies and monitoring.
By ensuring endpoint visibility, businesses can integrate endpoint security with SIEM systems for comprehensive threat hunting and response.
Cybersecurity Best Practices
To reduce vulnerabilities and protect against cyber threats, businesses should implement regular software updates, multi-factor authentication (MFA), employee training, and strong password policies. These cybersecurity practices ensure systems are secure, access is controlled, employees are aware of threats, and unauthorized access is minimized, significantly strengthening overall cybersecurity defenses.

Strong Passwords and Multi-factor Authentication (MFA)
Using strong passwords and multi-factor authentication (MFA) is essential for securing access to systems and sensitive data. Strong passwords make it harder for attackers to gain unauthorized access, while MFA adds an extra layer of protection by requiring multiple forms of verification, such as a password and a one-time code.
Important strategies for implementing strong security include:
- Password Complexity: Ensure passwords are long, unique, and contain a mix of characters to make them difficult to guess. For example, a password like “S!mp3L0g1n$” is more secure than a simple “password123”.
- Password Managers: Use tools like LastPass or 1Password to securely store and generate complex passwords, minimizing the risk of reusing weak passwords.
- MFA Methods: Implement MFA options like SMS-based codes, authenticator apps, or biometric authentication for additional security.
Regular Software Updates
Outdated software is one of the top causes of successful cyberattacks, as vulnerabilities in unpatched systems can be easily exploited by attackers. Keeping software up-to-date is essential for minimizing these risks and ensuring systems remain protected against known threats.
Effective strategies for maintaining secure systems include:
- Automatic Updates: Enable automatic updates for operating systems and applications to quickly address security flaws. For example, Windows Update automatically installs critical security patches as soon as they are available.
- Patch Management: Regularly review and apply patches for third-party applications, such as web browsers, plugins, or office suites, to close any security gaps.
- Security Scanning: Use tools like Qualys or Nessus to scan for outdated software and vulnerabilities that need patching.
Encryption
Securing data through encryption is essential for protecting sensitive information from unauthorized access during storage and transmission. By converting data into an unreadable format, encryption ensures that even if data is intercepted or accessed by attackers, it remains secure and unusable.
Key practices for implementing encryption include:
- AES-256 Encryption: A robust encryption standard that secures data both at rest and in transit, offering a high level of protection.
- TLS 1.3: The latest version of Transport Layer Security, which encrypts internet communications between users and websites.
- Key Rotation: Regularly updating encryption keys to prevent unauthorized access in case keys are compromised.
- Encryption at Rest vs. In-Transit: Ensuring data is encrypted when stored and when transmitted to protect it at every stage.
Firewalls and Anti-Virus Software
Installing firewalls and anti-virus software ensures the protection of critical systems against unauthorized access and malicious software. These tools are designed to monitor network traffic and detect harmful programs, preventing potential security breaches.
Some critical functions of these security tools include:
- Next-Generation Firewalls (NGFW): These firewalls go beyond simple packet filtering by inspecting application-level traffic and blocking more sophisticated attacks.
- Behavioral Anti-virus: Detects malicious activity based on behavior, enabling protection against new, unknown threats that signature-based software may miss.
- Update Frequency: Regular updates to both firewalls and anti-virus software ensure they can recognize and neutralize the latest threats.
- False Positive Handling: Adjusting security tools to reduce false positives, ensuring legitimate files and network traffic are not mistakenly flagged as threats.
VPN (Virtual Private Network)
Using a Virtual Private Network (VPN) is essential for securing internet traffic and ensuring data privacy, especially when working remotely or on public networks. A VPN encrypts your connection, making it much harder for hackers or unauthorized parties to intercept or access sensitive information.
Key features of a VPN include:
- IPsec Encryption: Encrypts data sent through the VPN, ensuring it is unreadable to anyone intercepting it.
- Split Tunneling: Allows certain traffic to bypass the VPN, improving performance while securing sensitive data.
- DNS Leak Protection: Ensures DNS queries are securely routed through the VPN, maintaining user privacy.
- Kill Switch: Disconnects the internet if the VPN connection drops, preventing exposure of data.
What are the Benefits of Cybersecurity for Your Business?
Cybersecurity is crucial for protecting your business from data breaches, financial loss, operational disruptions, and reputational damage. It ensures sensitive data remains secure, minimizes downtime caused by cyberattacks, and maintains customer trust. Strong cybersecurity practices also help with regulatory compliance, protect intellectual property, and enhance overall resilience, giving businesses a competitive advantage in the market.

Protection Against Financial Loss
Cyberattacks, such as ransomware, data breaches, or fraud, lead to direct financial costs, including remediation, legal fees, regulatory fines, and lost revenue. For example, the 2017 Equifax breach resulted in a $575 million loss in settlement, underscoring the immense financial impact of a data breach.
Preventive security investments like threat detection, incident response, and backup strategies help reduce these risks by minimizing the likelihood of successful attacks and limiting damage when incidents do occur. By addressing these threats proactively, businesses can lower financial risk, improve their valuation, boost investor confidence, and align with insurance requirements, ensuring financial protection and long-term stability.
Improved Customer Trust and Brand Reputation
Customers expect businesses to protect their data, and a single breach can destroy years of brand equity. The reputational damage from a breach can far exceed the immediate financial loss, as customers lose trust in the brand’s ability to protect their information.
Implementing robust cybersecurity measures, such as SSL certificates, transparent privacy policies, and visible compliance seals, can help build and maintain customer trust. Publicized breaches, on the other hand, can lead to lost trust, with 85% of customers abandoning a brand after a data breach, according to a PwC survey.
Companies that demonstrate digital trust not only protect their reputation but also build stronger relationships with customers, leading to higher loyalty, increased conversions, and differentiation in competitive markets.
Regulatory Compliance and Legal Protection
One of the key benefits of cybersecurity is ensuring compliance with industry regulations, which helps businesses avoid significant legal penalties and protect sensitive data. For example, failing to comply with GDPR can result in fines up to €20 million or 4% of global revenue. Implementing access controls, maintaining audit trails, and employing strong data protection measures like encryption are essential steps to meet these regulatory requirements.
By adhering to these regulations, businesses not only protect themselves from legal risks but also build customer trust, demonstrating their commitment to data privacy and security, which strengthens their overall reputation and business resilience.
Business Continuity and Operational Stability
Cybersecurity plays a crucial role in ensuring business continuity and minimizing disruptions during cyber incidents or system failures. According to MoldStud, establishing a solid incident response plan can reduce recovery time by up to 65%, enabling businesses to recover quickly and minimize downtime.
Key strategies like backup systems and failover mechanisms ensure services remain available, even when primary systems are compromised. By implementing these measures, businesses not only protect their operations but also maintain customer trust, demonstrating resilience in the face of disruptions. Strong cybersecurity practices are crucial for sustaining operations and protecting revenue, even during major incidents.
Competitive Advantage in the Market
A strong cybersecurity posture provides businesses with a competitive advantage by building trust and demonstrating reliability. Customers are more likely to choose companies that prioritize their data security, knowing that their sensitive information is protected.
For example, organizations with certifications like ISO 27001 or SOC 2 show potential clients that they adhere to strict security standards, which can be a key differentiator in competitive markets. Additionally, businesses that implement robust cybersecurity practices can gain a preference in procurement processes, especially in industries with high regulatory requirements, such as finance and healthcare. This proactive approach to security boosts customer confidence and sets businesses apart from competitors.
Cybersecurity Challenges
Businesses face several challenges in cybersecurity, including rapidly evolving threats, a lack of awareness, limited resources, and complex regulatory requirements. These challenges make it difficult to protect sensitive data, especially as cybercriminals continuously adapt their tactics and organizations struggle to stay ahead.
Evolving Threats
Cyber threats are constantly evolving, making it challenging for businesses to stay ahead of attackers. New attack methods, such as advanced malware, ransomware-as-a-service, and AI-powered phishing, are developed frequently, exploiting vulnerabilities faster than traditional security measures can address them. The rise of fileless attacks and zero-day exploits has further complicated defense efforts.
Businesses must invest in proactive threat intelligence and real-time monitoring to detect and mitigate these evolving risks, which require adaptable and multi-layered security strategies to remain effective.
Lack of Awareness
A lack of awareness about cybersecurity risks is one of the most significant challenges businesses face. Employees often unknowingly contribute to vulnerabilities, such as falling for phishing scams or neglecting basic security protocols.
Regular training programs and security awareness initiatives are essential to educate staff about the importance of cybersecurity and how to recognize potential threats. Implementing simple, effective policies like password management and identifying suspicious emails can significantly reduce the risk of human error and prevent cyberattacks.
Resource Constraints for Small Businesses
Small businesses often face significant challenges when it comes to cybersecurity due to limited resources, both in terms of budget and expertise. Without dedicated IT staff or access to advanced security tools, these businesses may struggle to protect their data and systems.
Outsourcing to Managed Security Service Providers (MSSPs) or adopting affordable cybersecurity frameworks, like CIS Controls, can help SMBs improve their security posture without the need for large upfront investments. Leveraging scalable and cost-effective solutions allows them to defend against cyber threats more effectively.
Regulatory Compliance
Meeting regulatory compliance requirements is another major cybersecurity challenge for businesses, especially those in highly regulated industries like healthcare, finance, and retail. Regulations such as GDPR, HIPAA, and PCI-DSS impose strict security standards to protect customer data, and failing to comply can result in hefty fines and reputational damage.
Implementing robust cybersecurity frameworks that align with these regulations, including data protection measures like encryption and access control, is essential for ensuring compliance and avoiding costly penalties. Regular audits and continuous monitoring are also critical to staying compliant.
Common Cybersecurity Tools
Cybersecurity tools, including firewalls, anti-virus software, intrusion detection systems (IDS), and endpoint protection platforms (EPP), are essential for detecting, preventing, and responding to cyber threats. By integrating these tools into a comprehensive security strategy, businesses can enhance threat detection, block unauthorized access, and respond to incidents more effectively, ensuring better protection against evolving cyber risks.
Firewalls
A firewall is a crucial tool in protecting networks by controlling incoming and outgoing traffic based on predefined security rules. It acts as a barrier between trusted internal networks and untrusted external networks, preventing malicious traffic from accessing sensitive systems. By configuring firewalls correctly, businesses can significantly reduce the risk of unauthorized access and cyber threats.
Key functions of firewalls include:
- Packet Filtering: Inspect each data packet and block any that do not meet the security rules, preventing harmful traffic from entering.
- Stateful Inspection: Monitors ongoing connections and only allows packets that are part of established, secure sessions.
- Next-Generation Firewalls (NGFW): Provide enhanced protection by combining traditional firewall features with advanced capabilities like intrusion prevention and application control.
Anti-virus and Anti-malware Programs
Protecting systems from malicious software is crucial to maintaining a secure network. Anti-virus and anti-malware programs play a vital role in detecting, preventing, and removing harmful software that can disrupt operations, steal sensitive data, or damage critical systems. These programs employ various detection methods, including signature-based detection, heuristic analysis, and real-time monitoring, to identify known and emerging threats.
| Feature | Anti-virus Programs | Anti-malware Programs |
| Primary Focus | Detection and removal of viruses | Broad protection against all types of malware, including ransomware and spyware |
| Detection Method | Signature-based detection | Signature-based and heuristic detection |
| Real-time Protection | Available in most anti-virus software | Often provides more comprehensive real-time monitoring |
| Types of Threats | Viruses, Trojans, and worms | Ransomware, spyware, adware, and more sophisticated threats |
| Scope of Protection | Limited to known threats | Protects against a wider range of evolving malware |
Network Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are essential for monitoring network traffic and identifying potential security threats in real-time. They analyze incoming and outgoing data for signs of malicious activity, such as unauthorized access attempts, malware infections, or data exfiltration. IDS can help businesses detect attacks early, allowing them to respond quickly and mitigate risks before any significant damage occurs.
Key features of IDS include:
- Network-based IDS (NIDS): Monitors network traffic for suspicious behavior, protecting large networks.
- Host-based IDS (HIDS): Installed on devices to monitor system activity for internal threats.
- Signature-based Detection: Detects known threats by comparing network traffic to pre-defined attack signatures.
- Anomaly-based Detection: Detects unusual traffic patterns, helping identify new or unknown threats.
Penetration Testing
Simulating real-world cyberattacks, penetration testing identifies vulnerabilities in systems, networks, and applications before they can be exploited by attackers. This proactive approach helps businesses pinpoint weaknesses and address them to prevent potential breaches.
The core aspects of penetration testing include:
- Reconnaissance: Gathering information about systems, networks, and targets to plan the attack strategy.
- Exploitation: Attempting to exploit vulnerabilities to gain unauthorized access to systems.
- Post-Exploitation: Determining the extent of access gained and potential impact, including data exfiltration.
- Reporting: Providing a detailed report of findings and recommendations for mitigating vulnerabilities.
Skills and Qualifications
Cybersecurity professionals require technical skills, industry certifications, and relevant qualifications to effectively defend against evolving cyber threats. For instance, expertise in network security, hands-on experience with firewalls, and certifications like CISSP are essential for success. As cyber threats grow more complex, both practical skills and recognized credentials are key to staying ahead in the field.
Essential Skills for Cybersecurity Professionals
Cybersecurity professionals need a strong foundation in various technical and analytical skills to effectively protect systems and data. Key skills include knowledge of network security, incident response, and proficiency in using security tools like firewalls and intrusion detection systems (IDS). Professionals should also be adept at risk assessment and vulnerability management, as well as understanding regulatory requirements such as GDPR and HIPAA.
Essential technical skills include:
- Threat Intelligence: Ability to analyze and respond to emerging cyber threats.
- Cryptography: Understanding encryption methods to secure data.
- Penetration Testing: Conducting tests to identify and fix security weaknesses.
- Security Operations: Managing and responding to security incidents effectively.
Key Certifications and Qualifications
Certifications and qualifications are crucial for cybersecurity professionals to prove their expertise and stay current with industry trends. They help validate a professional’s knowledge and ability to manage security risks, respond to incidents, and comply with industry regulations.
Some must-have certifications for cybersecurity professionals include:
- Certified Information Systems Security Professional (CISSP): Demonstrates advanced knowledge of information security concepts and practices.
- Certified Ethical Hacker (CEH): Validates skills in ethical hacking and penetration testing.
- CompTIA Security+: A foundational certification for IT professionals focusing on network security.
- Certified Cloud Security Professional (CCSP): Specializes in securing cloud environments.
- Offensive Security Certified Professional (OSCP): Focuses on hands-on penetration testing skills and real-world attack simulations.
- Microsoft SC-900: Specializes in Microsoft cloud security, offering skills to secure cloud environments and services.
In addition, relevant academic qualifications, such as a degree in information security or computer science, provide a solid technical foundation. These credentials help professionals gain credibility and meet employer expectations.
Importance of Continuous Learning in Cybersecurity
Continuous learning is essential for cybersecurity professionals to stay ahead of evolving threats and technologies. As cybercriminals develop new tactics, professionals must keep their skills up to date through ongoing education and hands-on practice. Participating in training labs, attending industry conferences, and renewing certifications ensures expertise in the latest tools and techniques.
Ways to maintain continuous learning include:
- Threat Intelligence Feeds: Staying updated on the latest security threats and vulnerabilities.
- Bug Bounty Programs: Participating in programs like HackerOne to practice real-world hacking and security testing.
- Hands-on Labs: Practicing on platforms like TryHackMe and Hack The Box to sharpen skills through real-time cybersecurity challenges.
- Certification Renewal: Earning CPE credits to maintain certifications like CISSP or CEH.
Careers and Jobs in Cybersecurity
As cyber threats continue to rise, businesses across all sectors, from healthcare to finance, are seeking skilled cybersecurity professionals. Roles like security analysts, penetration testers, security engineers, and compliance officers are in high demand. With organizations prioritizing digital security, these positions offer strong job stability, competitive salaries, and opportunities for growth in a rapidly expanding field.
Types of Cybersecurity Roles

The cybersecurity field offers a wide variety of roles, each focusing on different aspects of digital security. Professionals can specialize in protecting systems, testing vulnerabilities, or ensuring compliance with regulations. Key roles include:
- SOC Analysts: Monitor and protect an organization’s network and systems from cyber threats.
- Penetration Testers: Conduct simulated attacks to identify and fix security weaknesses in systems.
- Security Engineers: Design and implement security systems to protect against cyber threats.
- Compliance Officers: Ensure that an organization meets cybersecurity regulations and standards, such as GDPR or HIPAA.
- Cloud Security Architect: Focuses on securing cloud infrastructure and services, ensuring data protection and compliance in cloud environments.
Cybersecurity Job Market and Demand
The demand for cybersecurity professionals is growing rapidly across all sectors, driven by the increasing frequency and sophistication of cyber threats. For instance, employment of information security analysts is projected to grow 33% from 2023 to 2033, significantly outpacing the average job growth rate. This surge reflects the growing recognition of cybersecurity as a critical priority for businesses, governments, and other organizations.
A recent analysis by CyberSeek revealed that public and private sector employers sought over 514,000 cybersecurity jobs in the past 12 months, marking a 12% increase from the previous year. This spike demonstrates the heightened demand for skilled professionals to protect organizations from emerging threats.
According to the World Economic Forum’s Global Cybersecurity Outlook 2025, only 14% of organizations currently have the skilled talent needed to meet their cybersecurity objectives. This talent shortage is causing a significant gap in defense capabilities, further emphasizing the need for cybersecurity professionals.
In the U.S., the total number of workers employed in cybersecurity-related jobs has reached 1,337,400, and the cybersecurity job market continues to expand. As industries like healthcare, finance, and government increase their cybersecurity investments, the demand for qualified professionals remains high.
Average Salaries and Career Progression
Cybersecurity roles offer competitive salaries that vary depending on experience, certifications, and the level of responsibility. For entry-level positions like SOC analysts, the average salary typically starts at around $57,761 annually (ZipRecruiter). Mid-career roles, such as penetration testers or security engineers, can earn between $84,946 and $182,431 (Indeed), while senior roles like security architects or cloud security experts can command salaries in the range of $177,000 to $285,00 (Glassdoor).
Several factors influence these salary ranges, including certifications such as CISSP, CEH, and CompTIA Security+, as well as experience and expertise in specialized areas like cloud security or incident response. For instance, professionals with CISSP certification or experience in emerging technologies like AI security may see higher salaries. Location also plays a role, with cities like San Francisco or New York offering higher compensation due to the cost of living and high demand for talent.
Typical career progression paths in cybersecurity can start from a SOC analyst position, moving to an incident responder or security consultant, and ultimately advancing to senior roles like security architect or chief information security officer (CISO). As cybersecurity expertise becomes increasingly vital, salaries reflect the high demand for skilled professionals in the tech ecosystem.
How Much Do Managed Cybersecurity Services Cost?
Managed cybersecurity services typically range from $1,500 to $10,000+ per month, depending on the organization’s size, service complexity, and security needs. Smaller businesses may spend on the lower end for basic monitoring, while larger organizations with more extensive requirements, such as 24/7 monitoring and compliance, will face higher costs. These services offer robust protection while reducing the need for in-house cybersecurity teams.
Factors Influencing Managed Cybersecurity Service Costs
The cost of managed cybersecurity services depends on several factors, including the size of the organization, the complexity of the services, and the level of protection required. Larger businesses with complex security needs generally pay more for comprehensive services, while smaller businesses may pay less for basic solutions.
Key factors influencing costs include:
- Service Level Agreement (SLA): Higher-tier SLAs with faster response times and 24/7 support increase the cost.
- Monitoring Type: Continuous monitoring for threats or advanced services like endpoint protection or incident response adds to the price.
- Compliance Needs: Businesses needing to meet industry-specific regulations (e.g., HIPAA, GDPR) typically face higher costs for compliance-focused services.
- Geographic Coverage: Global businesses with multiple offices may require more extensive protection and localized support, raising costs.
Average Pricing Models for Managed Cybersecurity Services
Managed cybersecurity services are priced using different models, such as flat-rate, per-user, or per-device. Each model offers its own advantages depending on the company’s specific needs. Flat-rate pricing provides a fixed cost for services, while per-user or per-device models allow businesses to scale their services as they grow.
Here is a comparison of common pricing models:
| Pricing Model | Description | Cost Range | Best For |
| Flat-Rate | Fixed monthly fee for all services, regardless of usage. | $1,500 – $10,000/month | Businesses with predictable needs. |
| Per-User | Charges based on the number of users in the organization. | $150 – $350/user/month | Companies with a growing workforce. |
| Per-Device | Costs are based on the number of devices to be secured. | $50 – $150/device/month | Organizations with many endpoints to protect. |
| Tiered Services | Pricing depends on the level of service chosen (e.g., basic to advanced). | $50 – $250/device/month | Businesses needing flexible service options. |
ROI of Investing in Managed Cybersecurity Services
Investing in managed cybersecurity services offers a strong return on investment by preventing costly data breaches and ensuring business continuity. With cyber threats on the rise, the cost of recovering from a security incident, such as legal fees, fines, and reputational damage, often far exceeds the cost of preventive measures. Managed cybersecurity services help mitigate these risks, reducing downtime and the financial impact of cyberattacks.
Key ROI benefits include:
- Incident Cost Avoidance: Reduces the costs associated with data breaches, including legal fees, fines, and remediation efforts.
- Downtime Reduction: Minimizes service interruptions by ensuring systems remain secure and operational.
- Compliance Success Rate: Helps businesses stay compliant with regulations, avoiding penalties for non-compliance.
- SOC Efficiency: Enhances Security Operations Center (SOC) efficiency by quickly identifying and responding to threats.
The Future of Cybersecurity
As emerging technologies like AI, quantum computing, and blockchain continue to develop, their impact on cybersecurity will be profound. These advancements will drive the need for more sophisticated defense mechanisms, challenging existing encryption standards and changing how businesses approach data protection. Organizations will need to continuously adapt their strategies to mitigate evolving threats and safeguard against new vulnerabilities that these technologies could introduce.
AI in Cybersecurity
The integration of AI in cybersecurity will revolutionize how threats are detected, analyzed, and mitigated. AI-powered systems can process vast amounts of data in real time, identify emerging threats, and respond to incidents with unprecedented speed and accuracy. By automating routine security tasks and leveraging machine learning algorithms, AI can improve threat intelligence and reduce the workload on security teams.
Below are the benefits of AI in cybersecurity:
- Automated Threat Detection: By analyzing network traffic and user behavior, AI can identify unusual patterns, enabling rapid detection of potential cyber threats.
- Predictive Analytics: AI uses historical data to forecast cyberattacks, allowing businesses to proactively defend against emerging threats.
- Faster Incident Response: By automating responses to security incidents, AI system reduces the time it takes to mitigate damage and stop further breaches.
- Continuous Learning: Adapting and improving over time as AI learns from new data, enabling better detection of evolving threats.
Quantum Computing
Quantum computing has the potential to both challenge and enhance cybersecurity. On one hand, it could break current encryption methods, such as RSA encryption, by solving complex mathematical problems much faster than traditional computers. For example, a quantum computer could easily crack encryption used to secure sensitive data, posing a significant threat to data privacy.
On the other hand, quantum computing can also improve cybersecurity by enabling quantum cryptography, which offers unbreakable encryption methods. Quantum key distribution (QKD), for instance, uses quantum principles to secure data transmission, making it nearly impossible for attackers to intercept communication without being detected.
Blockchain for Cybersecurity
Blockchain enhances cybersecurity by offering decentralized solutions that improve data integrity and security. Unlike traditional centralized systems, blockchain distributes data across multiple nodes, making it more resistant to tampering and cyberattacks. Its transparency, immutability, and traceability are key features that ensure data protection.
Key applications of blockchain in cybersecurity include:
- Identity Verification: Provides secure, decentralized identity management, reducing the risk of identity theft.
- Data Integrity: Ensures that recorded data cannot be altered or deleted without detection.
- Secure Transactions: Enables transparent, tamper-proof transactions, especially in financial systems.
- Decentralized DNS: Prevents DNS hijacking by decentralizing DNS records.
The Rise of Cybersecurity Careers
As cyber threats continue to escalate, the demand for cybersecurity professionals is growing rapidly, creating numerous career opportunities. Organizations across all sectors need skilled experts to defend against increasingly sophisticated cyberattacks. This surge in demand makes cybersecurity one of the most promising and secure career fields, offering a variety of roles and high job stability.
Some job roles that have been sought out with the rise of cybersecurity include:
- Threat Hunter (Threat/Warning Analyst): Proactively searches for potential threats and vulnerabilities within networks.
- Red Teamer (Adversary Emulation Specialist): Simulates real-world attacks to test and improve an organization’s defenses.
- Digital Forensic Analyst: Investigates and analyzes cybercrimes, collecting evidence for legal action.
- Incident and Intrusion Analyst: Detects and responds to security incidents, minimizing damage from cyberattacks.
Conclusion
Cybersecurity is crucial for protecting businesses from a wide range of evolving threats that can disrupt operations, lead to financial losses, and damage reputations. By adopting best practices such as strong access controls, regular updates, and advanced threat detection systems, organizations can reduce risks and ensure operational continuity. The growing demand for cybersecurity professionals presents significant career opportunities in this rapidly expanding field. However, as cyber threats become increasingly complex, businesses must also recognize the need for managed cybersecurity services to maintain robust defenses. These services offer proactive protection, continuous monitoring, and expert response, ensuring organizations stay secure against emerging threats and minimizing the impact of potential breaches.



